by CIRT Team
Riltok mobile Trojan: A banker with global reach
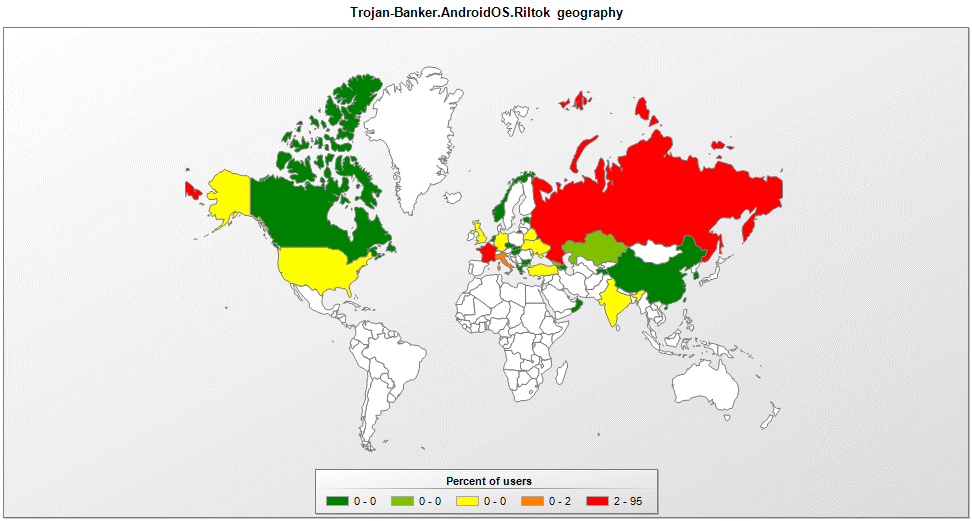
Kaspersky Lab researchers have identified a new variant of the Riltok mobile banking trojan that has been in operation since March 2018. The actors distributing Riltok have primarily focused on targeting individuals that reside in Russia, but versions for markets in France, Italy, Ukraine, and the United Kingdom have been detected in 2019. The trojan is distributed via SMS with a malicious link pointing to...
Read More
by CIRT Team
বিজিপি রুট লিক (BGP Route Leak) এবং প্রতিকারে সম্ভাব্য করণীয়
বিজিপি রুট লিক (BGP Route Leak) কি? ইন্টারনেট ইঞ্জিনিয়ারিং টাস্ক ফোর্স (আইইটিএফ/ IETF) এর RFC 7908 মতে বিজিপি রুট লিক (BGP Route Leak) নিমক্ত ভাবে সংজ্ঞায়িত করা হয়েছেঃ “The propagation of routing announcement(s) beyond their intended scope. That is, an announcement from an Autonomous System (AS) of a learned BGP route to another AS is in violation of the intended policies of the receiver, the...
Read More

by CIRT Team
High Commissioner of India, Dhaka visits BGD e-GOV CIRT Operations Center
High Commissioner of India, Ms Riva Ganguly Das has visited BGD e-GOV CIRT Security operations center on 19 June, 2019. She visited different components of BGD e-GOV CIRT and got briefed about the daily activities of security operations center, cycler censor activities, cyber range lab and digital forensic lab. Hon’ble state Minister Zunaid Ahmed Palak MP, Secretary of ICT Division N M Zeaul Alam, Executive...
Read More

by CIRT Team
BGD e-GOV CIRT has topped on Cybersecurity Drill – arranged by Sandia National Laboratories, US
Sandia National Laboratories Center for Global Security and Cooperation (operated by National Technology and Engineering Solutions of Sandia, LLC.) – Operated for the United States Department of Energy arranged two days hands on training on the “Countering DPRK Cyber Operations Workshop” held on 11 – 1 2 June 2019 at Dhaka, Bangladesh. The purpose of the workshop was to understand and prevent DPRK illicit cyber...
Read More
by CIRT Team
GlobeImposter 2.0 র্যানসমওয়্যার ও সতর্কতামূলক পদক্ষেপ
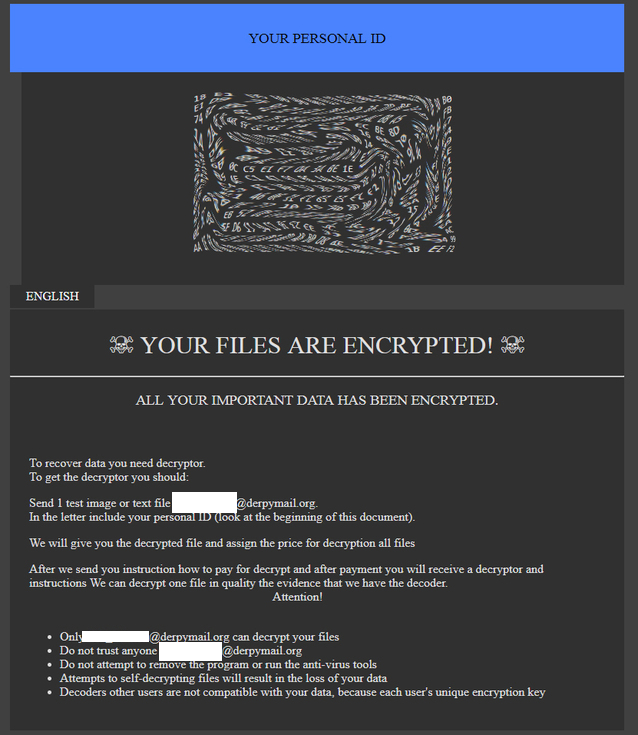
GlobeImposter 2.0 র্যানসমওয়্যার কি : সাইবার সিকিউরিটি গবেষকগন ২০১৮ সালে প্রথম GlobeImposter র্যানসমওয়্যার এর উপস্থিতি লক্ষ করেন যা GlobeImposter 1.0 নামে পরিচিত। কিন্তু বর্তমানে এর একটি নতুন সংস্করণ GlobeImposter 2.0 র্যানসমওয়্যার প্রকাশিত হয়েছে এবং দ্রুত সারা বিশ্বে ছড়িয়ে পড়েছে। এই সাম্প্রতিক আক্রমণে, সংক্রামিত কম্পিউটার সিস্টেম এর বিভিন্ন ফাইলগুলি এনক্রিপ্ট হচ্ছে, যা পুনরুদ্ধারের জন্য হ্যাকাররা অর্থ দাবি করছে। GlobeImposter 2.0 ফাইল এনক্রিপ্ট করার জন্য RSA +...
Read More
by CIRT Team
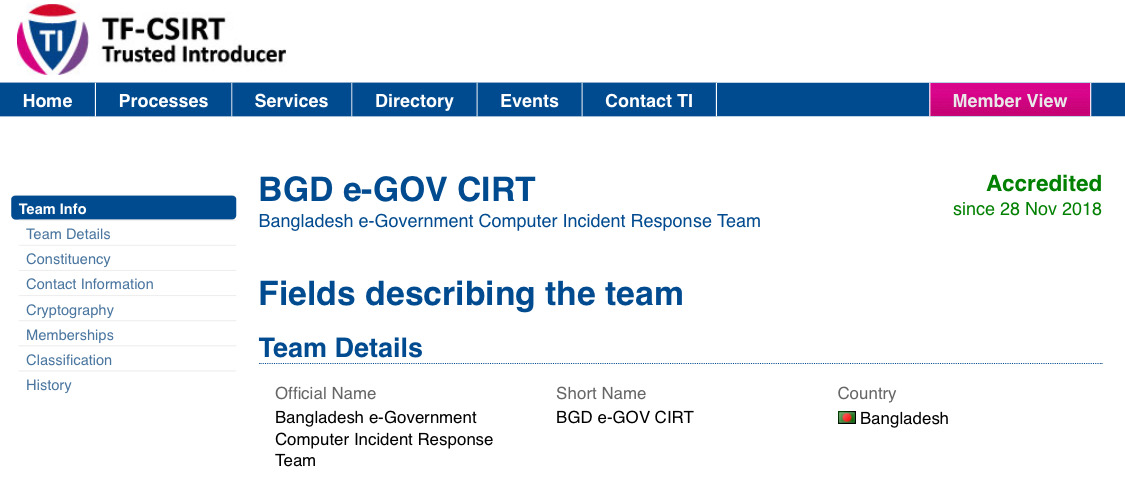
BGD e-GOV CIRT has become the Accredited Team of TF-CSIRT
The Trusted Introducer (TI) provides European CSIRTs (Computer Security Incident Response Teams) with a public repository that lists all known European CSIRTs and explains about the TI’s accreditation service. This service is meant to do just that: facilitate trust by formally accrediting CSIRTs that are ready to take that step. Earlier in September 2018, BGD e-GOV CIRT has been “listed” as Trusted Introducer of TF-CSIRT....
Read More

by CIRT Team
মেরিডিয়ান কমিউনিটিতে বাংলাদেশের পদার্পন
মেরিডিয়ান কমিউনিটি কি? “মেরিডিয়ান প্রসেস কমিউনিটি ” বিশ্বব্যাপী অবস্থিত ক্রিটিক্যাল ইনফরমেশন ইনফ্রাস্ট্রাকচার সমূহের সুরক্ষার (Critical Information Infrastructure Protection, CIIP) লক্ষ্যে সরকারি সংস্থাগুলোর মাঝে অভ্যন্তরীণ যোগাযোগ বৃদ্ধি, তথ্য ও ধারণা বিনিময় এবং সমস্যা নিরুপনের বিভিন্ন উপযোগী পদক্ষেপসমূহ নিয়ে কাজ করে থাকে। এই কমিউনিটি বিশ্বের বিভিন্ন দেশের সরকার ও সরকারি সংস্থাগুলোর মাঝে আন্তঃযোগাযোগ বৃদ্ধি, তাদের অভ্যন্তরীণ যোগাযোগ ও সহযোগিতার সুযোগ সৃষ্টি এবং সমস্যা সমাধানের জন্য প্রচলিত কর্মকান্ডগুলো...
Read More

by CIRT Team
How Facebook`s 50m user was hacked
When you log into your facebook using your id and password- you get an access token in return. These tokens are the equivalent of digital keys that keep people logged in to Facebook, so they don’t need to re-enter their password every time they use the app. This access token is used to prove your identity throughout all your activities in facebook- the likes/comments that...
Read More

by CIRT Team
ওআইসি-সার্ট কর্তৃক আয়োজিত সাইবার সিকিউরিটি ড্রিলে বিজিডি ই-গভ সার্টের অংশগ্রহণ
ওআইসি-সার্ট (The Organization of The Islamic Cooperation – Computer Emergency Response Teams, OIC-CERT) একটি নেতৃস্থানীয় আন্তর্জাতিক সংস্থা যার মূল লক্ষ্য হল সমগ্র বিশ্বব্যাপী সাইবার সুরক্ষা প্ল্যাটফর্ম তৈরিতে অগ্রণী ভূমিকা পালন করা এবং বিশ্বের বিভিন্ন সার্ট সংস্থাগুলোর মাঝে অভ্যন্তরীণ সহযোগিতার মাধ্যমে সাইবার হুমকিগুলো মোকাবেলা ও হ্রাস করা। ওআইসি-সার্ট প্রতি বছরই তার সদস্য সংস্থাগুলোর সক্ষমতা যাচাইয়ের লক্ষে সাইবার সিকিউরিটি ড্রিলের আয়োজন করে থাকে। বিশ্বের সাম্প্রতিক কোন একটি...
Read More

by CIRT Team
BGD e-GOV CIRT has successfully participated on OIC-CERT Cybersecurity Drill – 2018 with 75% Score
Background OIC-CERT CYBER SECURITY DRILL is an annual event for OIC-CERT members to build a better and secure Cybersecurity ecosystem, including the capacity in incident handling with suitable and comprehensive response as well as engaging better collaboration and coordination among CSIRT organizations from different countries. The final goal of this event is to get a more realistic experience in anticipating and handling some incidents related...
Read More










