by CIRT Team
Surge on Web Defacement and Web Application Related Vulnerabilities Targeting Bangladesh
Web defacement attacks and the exploitation of web application vulnerabilities are growing concerns in Bangladesh. These attacks, similar to virtual vandalism, involve hackers altering website appearances or content, often to embarrass site owners or promote personal agendas. Hackers also inject harmful code into websites, risking the security of visitor data. The exploitation of these vulnerabilities often leads to data breaches through exfiltration, dumping of personally...
Read More
by CIRT Team
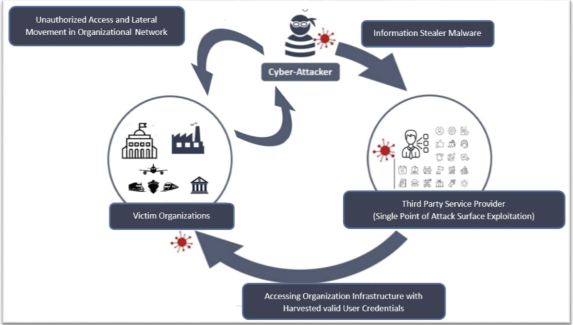
Cyber Threat Alert: Surge in Attacks via Compromised Third-Party Service Providers
The Cyber Threat Intelligence Unit at BGD e-GOV CIRT has identified a surge in cyber-attacks targeting organizations through the compromise of third-party service providers. Recently, multiple organizations in Bangladesh have encountered data breaches. Some individuals employed by third-party service providers, tasked with offering technical support to various client organizations, have been targeted by information-stealing malware. Investigations revealed that the information-stealing malware covertly extracted sensitive data,...
Read More

by CIRT Team
Training on cybersecurity awareness for Department of Women Affairs
As part of the regular activities of BGD e-GOV CIRT, training programs on diverse topics of cyber security and cyber awareness are conducted involving officials from various government and private organizations. Accordingly, several training sessions were organized with the participation of officials from Department of Women Affairs. October 11, 2023 Following topics were discussed during the sessions: Introduction to Cyber Security Importance of Awareness...
Read More
by CIRT Team
High Commissioner of India to Bangladesh visited BGD e-GOV CIRT
On 04 October 2023, H.E. Mr. Pranay Verma, High Commissioner of India to Bangladesh visited BGD e-GOV CIRT premises. CIRT team had the opportunity to briefly describe their operations and achievements. Mr. Zunaid Ahmed Palak MP, Honorable State Minister of ICT Division, Bangladesh, accompanied the team along with many other high officials.
by CIRT Team
Enhancing Situational Awareness on Emerging Cyber Threats
The Bangladesh Government’s Computer Incident Response Team (BGD e-GOV CIRT) carries out its primary mission of safeguarding the nation’s cyberspace through proactive management of computer security incidents and related activities. This mission involves close collaboration with international organizations and entities to effectively mitigate risks. Our goal is to maintain a continuous state of vigilance and preparedness, both in anticipation of potential incidents and in response...
Read More


by CIRT Team
Press Release: Situational Alert on Cyber Threats, June 2023
Here is the press release. Please click on the document below for full view.
by CIRT Team
Press release April 2023: Situational Security Alerts from CIRT
In the advent of EID holidays, Bangladesh Government’s Computer Incident Response Team (BGD e–Gov CIRT) would like to assure the security of the critical information infrastructures (CII), banks andfinancial institutions, health care and all sorts of government and private organizations by sharing alist of top threats to be vigilant for any suspicious activities in their infrastructure to prevent any sortof intrusion or disruption to their...
Read More
by CIRT Team
US Embassy Officials visited BGD e-GOV CIRT
James Gardiner, Economic Officer of the US Embassy in Bangladesh along with Shobhani Rasanayakam, an environment, science, technology, and health official of the US Embassy in Dhaka, as well as Asif Ahmed and Shila Ahmed, Economic Commercial Specialists visited BGD e-GOV CIRT premises on 13 April 2023. CIRT team had the opportunity to briefly describe their operations and achievements. Mr. Zunaid Ahmed Palak MP, Honorable...
Read More
by CIRT Team
Embassador of the Republic of China to Bangladesh visited BGD e-GOV CIRT
H.E. Mr. Yao Wen, Ambassador Extraordinary and Plenipotentiary of the People’s Republic of China to the People’s Republic of Bangladesh visited BGD e-GOV CIRT premises on 14 March 2023. CIRT team had the opportunity to briefly describe their operations and achievements. Mr. Zunaid Ahmed Palak MP, Honorable State Minister of ICT Division, accompanied the team along with many other high officials.









