How Facebook`s 50m user was hacked

by CIRT Team
When you log into your facebook using your id and password- you get an access token in return. These tokens are the equivalent of digital keys that keep people logged in to Facebook, so they don’t need to re-enter their password every time they use the app.
This access token is used to prove your identity throughout all your activities in facebook- the likes/comments that you do, the photos/videos you upload.

In 26 September, 50 millions user`s facebook login access token was compromised. It is the biggest security breach that facebook has encountered so far. So, how did that happen?
The answer lies in the ‘view as’ feature in facebook:
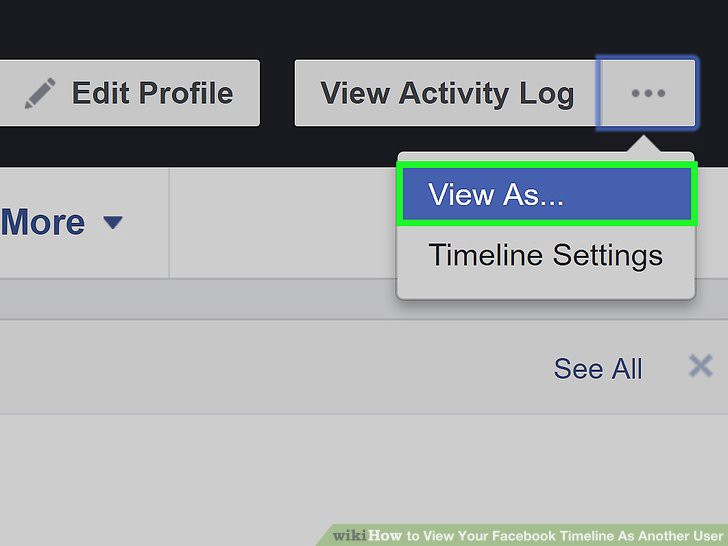
The ‘View As’ feature helps a user to view his profile from the eye of a specific person. People can type in any user name and see how that person sees what their profile looks like.
It is a combination of 3 bugs in ‘View As’ feature and ‘video-upload’ feature that helped the hackers spoof the access-tokens of the users:
In July 2017 facebook rolled out a new version of their video uploader, for faster uploading of videos. It is the lack of integration between this
‘View As’ feature and new ‘video-upload’ feature that lead to 3 bugs- which the attacker could tap into as the vulnerability point.
The 3 bugs are as follows:
1) The first bug was that when using the View As product,.View As should be a view-only interface. The video upload feature actually shouldn’t have showed up at all, when in ‘View As’ mode. But in a very specific case, around posts that encouraged people to wish Happy Birthday, it did show up.So, the View As incorrectly provided the opportunity to post a video.
2)The second bug was that this video uploader incorrectly used SSO(Single sign on) to generate an access token that had the permissions of the Facebook mobile app. That’s not how SSO was intended to be used on facebook: access-tokens were only meant to be created when users log-in.
3)The third bug was that when the video uploader showed up part as View As, it generated the access token not for you the actual user who is logged in, but for the specific person/user you were looking up , to preview your profile via the View As feature.
That seems like a fundamentally unsound design. Why should it even be theoretically possible for a request under the authority of one user to create a token with the authority of another user? And it had somehow missed the eyes of all the quality assurance engineers, penetration testers of facebook
So it’s the combination of these three bugs that created a vulnerability.And This vulnerability was discovered by hackers, and the way they exploited it is not just finding this vulnerability and using it to get an access token, but then every time they have an access token, pivoting from that to other accounts, to other friends to that user to get further access token. So in a span of a day, they could get access to 50 million users access token.

Stealing the access token is the worst possible attack, because it wouldn’t get logged or lead to any sort of notification. So the breach of access token means the hackers could get hold of all the personal informations: all their activities, personal messages, photos ,videos.
This ‘View As’ feature had a major security hole back in 2010, which let you view your friends live chats. Seems like it is giving facebook headache again.
Here is the techcrunch`s article from 2010 about that bug:
There is also one other major unanswered question about this incident is whether the access tokens could have let attackers interactively log in to third-party sites as the user. Tens of thousands of Web sites let users log in using nothing more than their Facebook profile credentials. If users have previously logged in at third-party sites using their Facebook profile, there’s a good chance the attackers could have had access to those third-party sites as well.

“We have a responsibility to protect your data, and if we can’t then we don’t deserve to serve you,”earlier this year , Zuckerberg wrote in a public apology regarding the Cambridge Analytica breach.
___________________________
Mahdi Mashrur Matin
CA Manager, National Data Center
Recommended Posts
Cyber Threat Alert: Surge in Attacks via Compromised Third-Party Service Providers
08 Feb 2024 - Articles, English articles, Security Advisories & Alerts