Riltok mobile Trojan: A banker with global reach
by CIRT Team
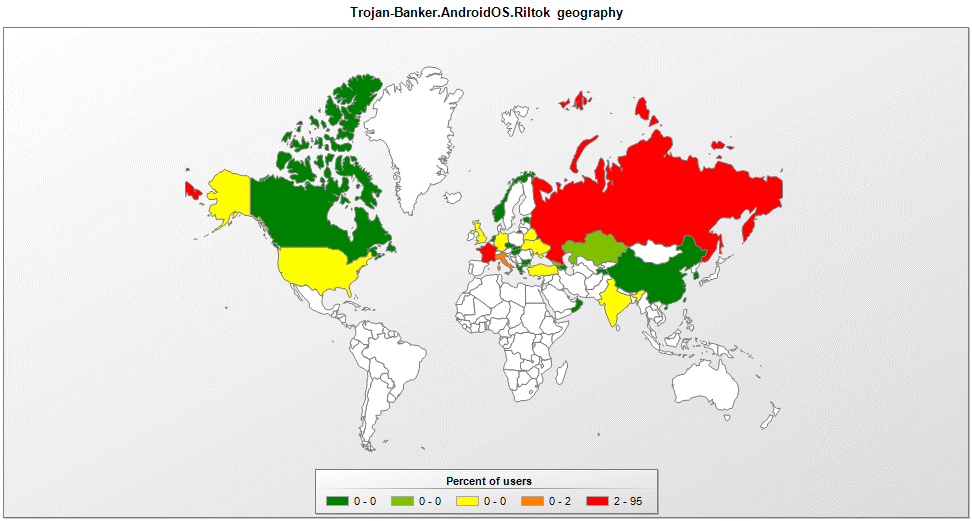
Kaspersky Lab researchers have identified a new variant of the Riltok mobile banking trojan that has been in operation since March 2018. The actors distributing Riltok have primarily focused on targeting individuals that reside in Russia, but versions for markets in France, Italy, Ukraine, and the United Kingdom have been detected in 2019. The trojan is distributed via SMS with a malicious link pointing to a fake website that simulates an ad-free version of one of the following popular mobile apps: Avito, Youla, Gumtree, Leboncoin, or Subito. During installation of the imitated app, Riltok asks the user for permission to use special features within the AccessibilityService, which then allows Riltok to prompt users with fake payment screens requesting bank card information. Once Riltok performs basic validation on the bank card details, the information is directed back to the criminal’s Command and Control (C2) server. Additionally, the trojan can hide notifications from certain banking apps installed on the device.

Geographic spread of the Riltok banking Trojan
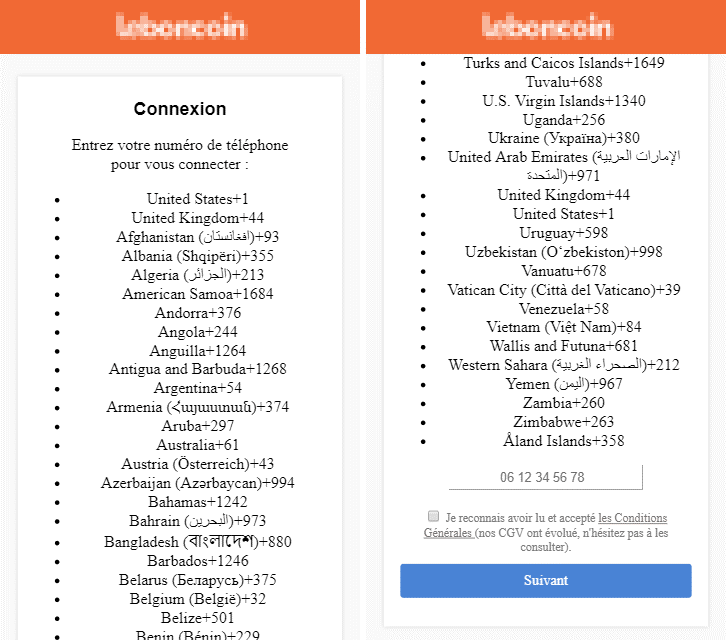
Phishing page from the French version of the Trojan
Riltok actively communicates with its C&C server. First off, it registers the infected device in the administrative panel by sending a GET request to the relative address gate.php (in later versions gating.php) with the ID (device identifier generated by the setPsuedoID function in a pseudo-random way based on the device IMEI) and screen(shows if the device is active, possible values are “on”, “off”, “none”) parameters.
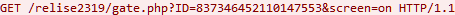
Then, using POST requests to the relative address report.php, it sends data about the device (IMEI, phone number, country, mobile operator, phone model, availability of root rights, OS version), list of contacts, list of installed apps, incoming SMS, and other information. From the server, the Trojan receives commands (for example, to send SMS) and changes in the configuration.
Recommendation: Threats are better prevented than cured. Avoid following suspicious links in SMS, and be sure to install apps only from official sources. In addition, check what permissions you are granting during the installation of any app. As Riltok shows, threat actors can apply the same methods of infection to victims in different countries with more or less the same success.
Reference: https://securelist.com/mobile-banker-riltok/91374/










