by CIRT Team
Cybercriminals focus on the shipping and cloud storage sectors [source: helpnetsecurity]
The Anti-Phishing Working Group’s latest report found upticks in phishing attacks against companies in the Logistics & Shipping as well Cloud Storage & File Hosting sectors, mounted by cyber gangs against the accounts of both individuals and enterprises. Once they steal usernames and passwords, the criminals can then steal not only funds, but also use services to spend spam mail, order goods for resale, and other...
Read More
by CIRT Team
APT Activity Targeting Energy and Other Critical Infrastructure Sectors [source: us-cert]
Systems Affected Domain Controllers File Servers Email Servers Overview This joint Technical Alert (TA) is the result of analytic efforts between the Department of Homeland Security (DHS) and the Federal Bureau of Investigation (FBI). This alert provides information on advanced persistent threat (APT) actions targeting government entities and organizations in the energy, nuclear, water, aviation, and critical manufacturing sectors. Working with U.S. and international partners,...
Read More
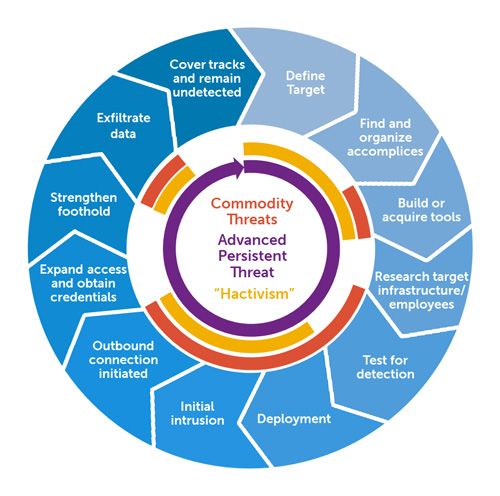
by CIRT Team
সতর্কতামুলক বার্তা : Advanced Persistent Threat (APT) ও Critical Infrastructure সমূহ
বর্তমানে সাইবার জগতের আলোচিত বিষয় হচ্ছে Advanced Persistent Threat (APT) এবং APT সাইবার হুমকির অন্যতম লক্ষ্যবস্তু হচ্ছে গুরুত্বপূর্ণ সরকারী স্থাপনা বা Critical Infrastructure সমূহ। সাইবার আক্রমণকারীরা প্রতিনিয়ত তাদের কর্মপন্থা পরিবর্তন করে যাচ্ছে যাতে তাদের কার্যকলাপ সনাক্ত করা না যায়। APT-এর উপর পরিচালিত এক গবেষণা থেকে জানা যায়, সাইবার আক্রমণকারীরা বৈধ (legitimate) ও আপাত দৃষ্টিতে সাধারন ই-মেইল এর মাধ্যমে Malware বিতরণ (distribution) করবার চেষ্টা করছে। Figure...
Read More

by CIRT Team
Member of the Board of Directors of FIRST.org visits BGD e-GOV CIRT
Member of the Board of Directors of FIRST.Org, Inc and Senior Internet Security Specialist of APNIC Mr. Adli Wahid has visited BGD e-GOV CIRT Headquarter situated in ICT Tower, Dhaka today (23 October 2017). During his presence in BGD e-GOV CIRT, he attended in a friendly meeting with CIRT Team, represented by Mr. Tawhidur Rahman, Team Leader, BGD e-GOV CIRT. He also attended in two...
Read More

by CIRT Team
Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2
On October 16th, 2017, a research paper with the title of “Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2” was made publicly available. This paper discusses seven vulnerabilities affecting session key negotiation in both the Wi-Fi Protected Access (WPA) and the Wi-Fi Protected Access II (WPA2) protocols. These vulnerabilities may allow the reinstallation of a pairwise transient key, a group key, or an integrity key...
Read More
by CIRT Team
Unauthorized Coin Mining in the Browser [source: paloaltonetworks]
Cryptocurrencies have taken the world by storm. From the biggest player Bitcoin to newcomers such as Monero and Ethereum, cryptocurrency mining has become a hot industry due in part to powerful, dedicated mining hardware or by utilizing graphics cards’ parallel computing power. Recently, browser coin mining has taken off, for a lot of different reasons. Although the computing power per instance is much less than...
Read More
by CIRT Team
A Gigantic IoT Botnet Has Grown in the Shadows in the Past Month [source: bleepingcomputer]
Since mid-September, a new IoT botnet has grown to massive proportions. Codenamed IoT_reaper (Reaper for this article), researchers estimate its current size at nearly two million infected devices. According to researchers, the botnet is mainly made up of IP-based security cameras, network video recorders (NVRs), and digital video recorders (DVRs). Based on Mirai, but not a Mirai offspring Researchers from Chinese security firm Qihoo 360...
Read More
by CIRT Team
A Look at Locky Ransomware’s Recent Spam Activities [source: trendmicro]
Ransomware has been one of the most prevalent, prolific, and pervasive threats in the 2017 threat landscape, with financial losses among enterprises and end users now likely to have reached billions of dollars. Locky ransomware, in particular, has come a long way since first emerging in early 2016. Despite the number of times it apparently spent in hiatus, Locky remains a relevant and credible threat given its impact on end users and especially...
Read More
by CIRT Team
88 Percent of Java Apps Susceptible to Widespread Attacks [source: itsecurityguru]
Veracode, Inc., a leader in securing the world’s software, and acquired by CA Technologies (NASDAQ:CA), today announced findings from the 2017 State of Software Security Report, a comprehensive review of application security testing data from scans conducted by CA Veracode’s base of more than 1,400 customers. Among other industry trends such as vulnerability fix rates and percent of applications with vulnerabilities, the report exposes the pervasive risk...
Read More
by CIRT Team
ARP Spoofing Used to Insert Malicious Adverts [source: alienvault]
Recently we came across a new variant of the malware ServStart. ServStart is primarily used by attackers located in China, in a mix of targeted and opportunistic attacks. The attackers are hosting the ServStart malware on a file server that is open for anyone to view. A report from 2014 for an attack involving CVE-2014-6332 describes how an attacker might use zxarps well: “This malware performs ARP spoofing...
Read More









