
by CIRT Team
Training on cybersecurity awareness for Department of Women Affairs
As part of the regular activities of BGD e-GOV CIRT, training programs on diverse topics of cyber security and cyber awareness are conducted involving officials from various government and private organizations. Accordingly, several training sessions were organized with the participation of officials from Department of Women Affairs. October 11, 2023 Following topics were discussed during the sessions: Introduction to Cyber Security Importance of Awareness...
Read More
by CIRT Team
BGD e-GOV CIRT এর আয়োজনে আয়োজনে আর্থিক প্রতিষ্ঠান ও CII সমূহের সাইবার ড্রিল ২০২৩ চূড়ান্ত পর্ব অনুষ্ঠিত
বাংলাদেশ সরকারের জাতীয় কম্পিউটার ইনসিডেন্ট রেসপন্স টিম BGD e-GOV CIRT এর সার্বিক তত্ত্বাবধানে ২১ অক্টোবর ২০২৩ তারিখ (শনিবার) গুরুত্বপূর্ণ তথ্য পরিকাঠামোসমূহ এবং আর্থিক প্রতিষ্ঠানসমূহের কর্মকর্তাদের অংশগ্রহণে Financial Institute & CIIs Cyber Drill 2023 এর চূড়ান্ত পর্ব Military Institute of Science and Technology (MIST) প্রাঙ্গণে অনুষ্ঠিত হয়েছে। দুইটি ধাপে আয়োজিত এই সাইবার ড্রিল এর প্রাথমিক বাছাই পর্ব গত ০৭ অক্টোবর ২০২৩ তারিখ অনলাইনে অনুষ্ঠিত হয়। প্রথম...
Read More
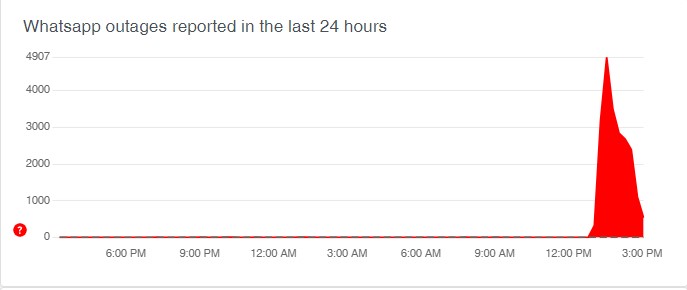
WhatsApp down for millions of users globally: App not working for group and individual chats; Twitter gets flooded with memes
Instant messaging app WhatsApp is down since 12.30 pm today as users are not able to send messages to group chats and only one tick was showing to messages sent to individuals. The messages sent to Group chats are not being delivered. Many WhatsApp users reported facing issues with their chats globally. Not only smartphone users but even WhatsApp web and WhatsApp desktop apps were...
Read More
by CIRT Team
সাইবার-নিরাপত্তা-সূচকে-এগিয়েছে-বাংলাদেশ
https://www.ittefaq.com.bd/national/255892/সাইবার-নিরাপত্তা-সূচকে-এগিয়েছে-বাংলাদেশhttps://www.prothomalo.com/bangladesh/বৈশ্বিক-সাইবার-নিরাপত্তা-সূচক-এগোল-বাংলাদেশhttps://bangla.bdnews24.com/tech/article1908304.bdnewshttps://somoynews.tv/news/2021-06-29/সাইবার-নিরাপত্তা-সূচকে-বাংলাদেশের-দারুণ-অগ্রগতিhttps://www.banglatribune.com/688130/আন্তর্জাতিক-সাইবার-নিরাপত্তা-সূচকে-২৫-ধাপ-এগিয়েছেhttps://www.bd-journal.com/information-technology/165109/আন্তর্জাতিক-সাইবার-নিরাপত্তা-সূচকে-২৫-ধাপ-উন্নতি-বাংলাদেশেরhttps://www.amadershomoy.com/bn/2021/06/30/1400602.asphttp://bartabazar.com/archives/316736https://www.ppbd.news/feature/sci-tech/206355/সাইবার-নিরাপত্তা-সূচকে-বাংলাদেশের-২৫-ধাপ-উন্নতিhttps://sarabangla.net/post/sb-567504/https://www.dhakapost.com/technology/42814https://digibangla.tech/news/local/telecom/53028/https://www.unb.com.bd/category/Bangladesh/bangladesh-moves-25-spots-up-in-global-cybersecurity-index/74711
by CIRT Team
BlockThreat – Week 26, 2020
Another week, another DeFi exploit or two. Unfortunately, this time the bad folks were able to steal $500k worth of tokens. It’s too bad Balancer devs dismissed an earlier bug bounty report. ClearSky released a detailed report on CryptoCore APT which is dedicated to breaking into cryptocurrency exchanges. On a more fun side checkout someone almost getting caught by a honeypot smart contract and submit your...
Read More










