There are many ways to define “Critical Infrastructure,” but what these definitions have in common is most closely conceived of as infrastructure that would affect the economic and national security of a country if it were negatively impacted or eliminated. The U.S. Department of Homeland Security describes critical infrastructure as the resources, structures, and networks, either physical or electronic, so important to the U.S. that...
Read More
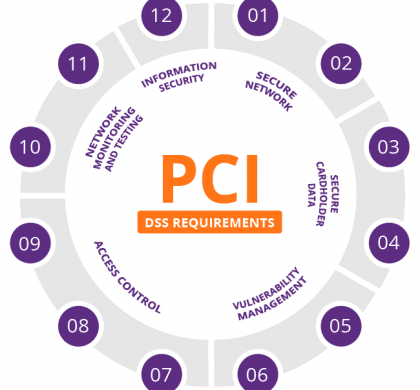
What is PCI DSS? The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards formed in 2004 by Visa, MasterCard, Discover Financial Services, JCB International and American Express. Governed by the Payment Card Industry Security Standards Council (PCI SSC), the compliance scheme aims to secure credit and debit card transactions against data theft and fraud. While the PCI SSC has...
Read More
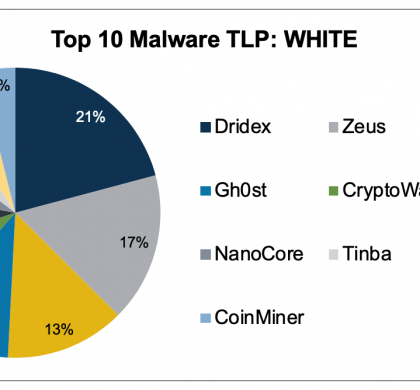
Top 10 Malware composition was consistent with February 2020 with the exception of Pushdo and Tinba. Overall, the Top 10 Malware variants comprised 42% of Total Malware activity in March, down from 51% in January. It is highly likely that Dridex, Gh0st, Kovter, and ZueS will continue to make up a significant portion of the Top 10 Malware. In March 2020, malware delivered via malspam...
Read More
Dated : 11 March 2020 The Asia Pacific Computer Emergency Response Team (APCERT) today has successfully completed its annual drill to test the response capability of leading Computer Security Incident Response Teams (CSIRT) within the Asia Pacific economies. The theme of this year’s APCERT Drill is “Banker doubles down on Miner”. This exercise reflects real incidents and issues that exist on the Internet. The participants...
Read More
The Effect of Geopolitics on Cybersecurity Technological growth and its breakthrough advances, along with their advantages, also have disadvantages, which are obvious examples of communication equipment. In fact, today, the Internet, telephones, cell phones and other communication devices can be described as a double-edged sword used to facilitate communications on the one hand and to spy on and monitor information. The main pillar of cyber...
Read More