For a long period of time phishing is one of the major cyber threats in cyberspace. Phishing is the fraudulent attempt to obtain sensitive information such as usernames, passwords and credit card details by disguising oneself as a trustworthy entity in an electronic communication.[1] For past few years we have noticed a rise in the phishing attack in all part of the globe. Anti Phishing...
Read More
Secure Socket Layer (SSL) is a protocol that provides security for communications between client and server by implementing encrypted data and certificate-based authentication. If you’re using Apache Tomcat as a Server for your web-application , chances are that at least some of the data you’re handling is sensitive, and SSL is an easy way to offer your users security. But the configuration process and SSL...
Read More
Introduction The Common Weakness Enumeration (CWE™) Top 25 Most Dangerous Software Errors (CWE Top 25) is a demonstrative list of the most widespread and critical weaknesses that can lead to serious vulnerabilities in software. These weaknesses are often easy to find and exploit. They are dangerous because they will frequently allow adversaries to completely take over execution of software, steal data, or prevent the software...
Read More
What are the risks associated with mobile device apps? Applications (apps) on your smartphone or other mobile devices can be convenient tools to access the news, get directions, pick up a ride share, or play games. But these tools can also put your privacy at risk. When you download an app, it may ask for permission to access personal information—such as email contacts, calendar inputs,...
Read More
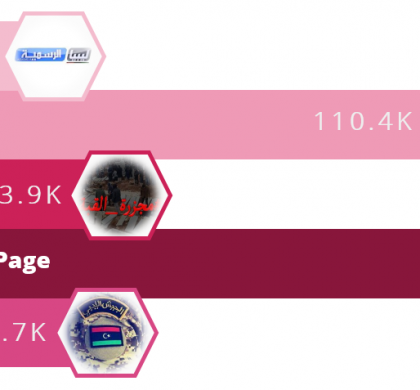
A large-scale campaign has been distributing malware on Facebook for an unspecified number of years primarily targeting the country of Libya, according to Check Point researchers. The threat actors behind this campaign are utilizing the geopolitical and political pages themed around Libya that attempt to convince individuals to download malicious files. Researchers identified more than 30 Facebook pages distributing malicious links and some of the...
Read More



![2019 CWE Top 25 Most Dangerous Software Errors [mitre]](https://www.cirt.gov.bd/wp-content/uploads/2019/09/2019CWETop25-420x390.png)