PCI DSS: Basic Information, Certification, Compliance level & Requirement
by CIRT Team
What is PCI DSS?
The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards formed in 2004 by Visa, MasterCard, Discover Financial Services, JCB International and American Express. Governed by the Payment Card Industry Security Standards Council (PCI SSC), the compliance scheme aims to secure credit and debit card transactions against data theft and fraud.
While the PCI SSC has no legal authority to compel compliance, it is a requirement for any business that processes credit or debit card transactions. PCI certification is also considered the best way to safeguard sensitive data and information, thereby helping businesses build long lasting and trusting relationships with their customers.
The monetary results of this fraud alone are daunting, yet there are further consequences of not protecting sensitive cardholder data, including:
- The client losing confidence
- The cost of reissuing new payment cards
- Higher subsequent costs of compliance
- Legal costs, settlements, and judgments
- Fines and penalties
- Termination of your client’s ability to accept payment cards
- Lost jobs
- Bankruptcy or even going out of business
What Does PCI DSS Impact?
PCI DSS applies to all businesses that store, process, or transmit cardholder data and/or sensitive authentication data. If a business outsources its payment processing to a third party, the business is responsible for ensuring that the account data is adequately protected by that third party as required by PCI DSS requirements.
PCI DSS is designed to protect cardholder’s sensitive information by ensuring the processes, people and systems that access the data have adequate controls around their usage.
Cardholder data and sensitive authentication data is defined as follows:
- Cardholder Data includes,
- Primary Account Number (PAN)
- Cardholder Name
- Expiration Date, and
- Service Code
- Sensitive Authentication Data includes full track data (magnetic-stripe data or the equivalent data contained on a chip), CAV2/CVC2/CVV2/CID, and PINs or PIN blocks.
- CVV2 (Card Verification Value 2, for Visa)
- CVC2 (Card Validation Code 2, for MasterCard), and
- CID (Card Identification Number, for American Express)
- The PAN is the critical element associated with cardholder data. If the cardholder name, service code and/or expiration date are stored, processed or transmitted with the PAN, or are existing there in the cardholder data environment (CDE), they must be guarded in accordance with PCI DSS requirements
Visa and MasterCard
- For Visa and MasterCard, it is a three-digit value that is usually printed in reverse italics and featured on the right side of the signature line on the back of the card.

CVV2 code on the back of a Visa credit card
American Express
- For American Express cards, it is a four-digit card verification value that can be found on the front of the card just above the card number.

CID code on the front of an Amex card
Where Does Sensitive Data Loss Occur?
Cardholder data and sensitive authentication data loss can occur in multiple areas and in numerous scenarios, including:
- Compromised card reader
- Point of sale system
- Storage networks
- Database
- Online portals
- Wireless routers
- Filing cabinet
- Varying electronic eavesdropping methods (e.g., hidden cameras or wiretap
- Backup Data (Data in Rest)
PCI DSS Compliance levels:
PCI compliance is divided into four levels, based on the annual number of credit or debit card transactions a business processes. The classification level determines what an enterprise needs to do to remain compliant.
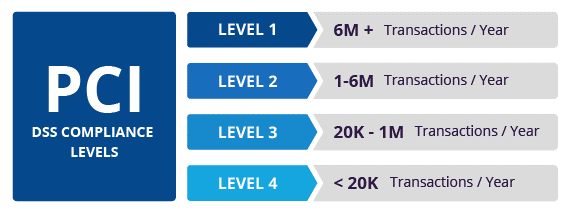
- Level 1: Applies to merchants processing more than six million real-world credit or debit card transactions annually. Conducted by an authorized PCI auditor, they must undergo an internal audit once a year. In addition, once a quarter they must submit to a PCI scan by an Approved Scanning Vendor (ASV).
- Level 2: Applies to merchants processing between one and six million real-world credit or debit card transactions annually. They’re required to complete an assessment once a year using a Self-Assessment Questionnaire (SAQ). Additionally, a quarterly PCI scan may be required.
- Level 3: Applies to merchants processing between 20,000 and one million e-commerce transactions annually. They must complete a yearly assessment using the relevant SAQ. A quarterly PCI scan may also be required.
- Level 4: Applies to merchants processing fewer than 20,000 e-commerce transactions annually, or those that process up to one million real-world transactions. A yearly assessment using the relevant SAQ must be completed and a quarterly PCI scan may be required.
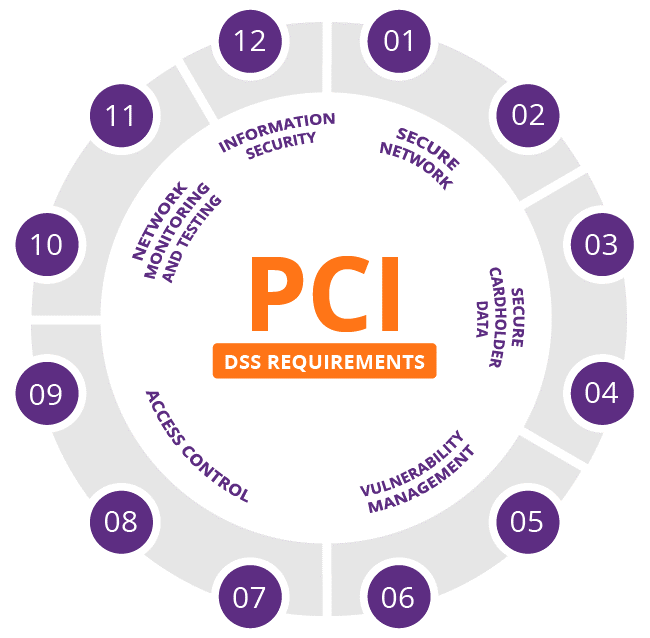
PCI DSS requirements:
The PCI SSC has outlined 12 requirements for handling cardholder data and maintaining a secure network. Distributed between six broader goals, all are necessary for an enterprise to become compliant.

Secure network
- Install and maintain a firewall configuration to protect cardholder data:
Firewalls are a vital component of any computer network and are the first line of defense for Internet traffic. A firewall identifies all network traffic and blocks any transmissions that don’t meet the business’s specified security criteria. All systems must be protected from unauthorized access from untrusted networks—regardless of the method of entry (e.g., Internet e-commerce, employee Internet access, employee e-mail access, business-to-business connections or wireless networks). Mostly firewall operate at Network and transport layers (layers 3 and 4) of OSI model. Firewall failure are most commonly caused by human error and misconfiguration.
- Do not use vendor-supplied defaults for system passwords and other security parameters:
Criminals and data thieves use vendor default passwords and default settings to compromise systems. It is critically important to change vendor-supplied default passwords/settings and remove/disable unnecessary default accounts before introducing new systems into your environment. Some Organization use new service introduction process to impose control to reduce such risk.
Secure cardholder data
- Stored cardholder data must be protected:
There are many methods of protecting your client’s sensitive data: encryption, truncation, masking, and hashing can each become a critical component of your business’s cardholder data protection plan. Additionally, don’t store cardholder data unless necessary, and don’t send unprotected information via e-mail. To understand the basic of encryption, one need to go through symmetric and asymmetric cryptography and their standard/mode/algorithm.
- Transmissions of cardholder data across public networks must be encrypted:
Cardholder’s sensitive data and authentication information must be encrypted during transmission over open, public networks. These networks are targeted by individuals who exploit the open, visible nature of the network to gain unauthorized system access. There are two types of encryption
Vulnerability management
- Anti-virus software must be used and regularly updated:
Malware is malicious software that can be introduced into your network during any typical business activity, such as employee e-mail, Internet usage, using personal employee computers, cell phones or by utilizing an infected storage device such as a USB drive.
Antivirus software must be installed and operating on all business systems to protect your client’s environments. The security software must be correctly configured and maintained as there are constantly evolving malicious software threats found every day.
- Secure systems and applications must be developed and maintained:
Intruders use security vulnerabilities in your systems and applications to gain privileged access to cardholder sensitive data. These security vulnerabilities are typically remediated through the application of security patches (typically provided by the vendor), and must be installed by whoever manages those systems.
Implement Strong Access control
- Cardholder data access must be restricted to a business need-to-know basis
Role-based access control (RBAC) is a method of restricting network access based on the roles of individual users. The more people who have access to cardholder data, the higher chance you have of a breach.
- Every person with computer access must be assigned a unique ID
Almost all POS systems and PCI compliant software give you the option to assign Unique IDs for each user or employee. Make this a habit so you can track down exactly who was using what and when at any time. So, log retention is important part as well.
- Physical access to cardholder data must be restricted
Only qualified and approved employees should be interacting with cardholder data at any point.
Network monitoring and testing
- Access to cardholder data and network resources must be tracked and monitored
One of the example like make sure you have cameras set up and have all terminals within clear view. This discourages fraudulent activity. Video cameras/Close Circuit Television(CCTV) are physical control as well as deterrent and preventive controls as per security control perspective.
- Security systems and processes must be regularly tested
The easiest way to approach this guideline is to have employees sign off on the completion of the test at regular intervals and make the system security health check as a routine work. Make this a part of the job from the beginning.
Information security
- Maintain a policy that addresses information security for all personnel
Part of what auditors look for is proof that you are taking all of the guidelines into account, and the most common way to prove you are being by developing and executing a security policy that covers all of the guidelines/procedures/SOP’s. Make this your central space for everything PCI, from running scans to employee guidelines etc.
Reference:
- https://www.imperva.com/learn/data-security/pci-dss-certification/
- https://tidalcommerce.com/learn/pci-compliance-checklist
- https://www.anuko.com/store/what_is_cvv2.htm
- https://www.solarwindsmsp.com/content/pci-dss-requirements-checklist
- PCI DSS Quick Reference Guide
- CISSP, Sybex, Eight Edition, Mike Chapple, James Micheal Stewart, Darril Gibson
Muhammad Moinul Hossain CISM, CISA, ISMS Auditor, ITIL, ENSA
IT Auditor
Strengthening of BGD e-GOV CIRT & NCIRT
Bangladesh Computer Council (BCC)









