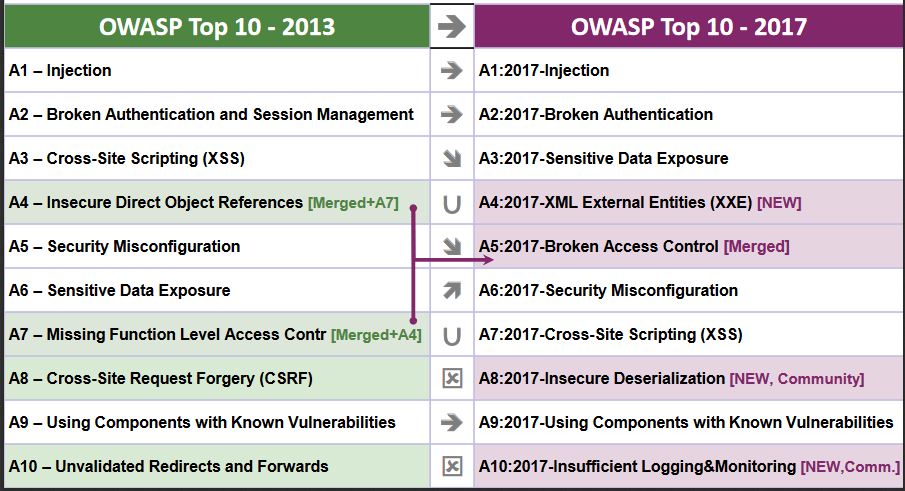
The Open Web Application Security Project (OWASP) has officially released its Top 10 most critical web application security risks four years after its last update, in 2013. As in previous years, injection remained the top application security risk, but there has been some shuffling in the ranking, with the appearance of three newcomers — XML External Entities (XXE), Insecure Deserialization and Insufficient Logging & Monitoring....
Read More
Description: An authentication bypass vulnerability in Juniper Networks Junos Space Network Management Platform may allow a remote unauthenticated network based attacker to login as any privileged user. This issue only affects Junos Space Network Management Platform 17.1R1 without Patch v1 and 16.1 releases prior to 16.1R3 Impact: An attacker can exploit this issue to bypass the authentication mechanism and perform unauthorized actions. This may lead...
Read More
Description: A vulnerability in the Smart Licensing Manager service of the Cisco Firepower 4100 Series Next-Generation Firewall (NGFW) and Firepower 9300 Security Appliance could allow an authenticated, remote attacker to inject arbitrary commands that could be executed with root privileges. The vulnerability is due to insufficient input validation of certain Smart Licensing configuration parameters. An authenticated attacker could exploit the vulnerability by configuring a malicious...
Read More
Description: The vulnerability exists due to insufficient sanitization of user-supplied parameters that are passed to certain Python functions within the scripting sandbox of the affected device. An attacker could exploit this vulnerability to escape the scripting sandbox and execute arbitrary commands on the underlying operating system with the privileges of the authenticated user. To exploit this vulnerability, an attacker must have local access and be...
Read More
Description: Cisco ASA Next-Generation Firewall Services is prone to a remote security-bypass vulnerability. Impact: Successfully exploiting this issue may allow an attacker to bypass certain security restrictions and perform unauthorized actions. This issue is being tracked by Cisco Bug CSCvd97962. Mitigation: Updates are available. Please see the references or vendor advisory for more information. Reference URL’s: http://www.securityfocus.com/bid/101915/info https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20171115-firepower1
Description: WPA2 is prone to multiple security weaknesses. Impact: Exploiting these issues may allow an unauthorized user to intercept and manipulate data or disclose sensitive information. This may aid in further attacks. Mitigation: Updates are available. Please see the references or vendor advisory for more information. Reference URL’s: https://www.krackattacks.com/ https://ics-cert.us-cert.gov/advisories/ICSA-17-318-01 https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2017-13080 https://security-center.intel.com/advisory.aspx?intelid=INTEL-SA-00101&languageid=en-fr https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20171016-wpa https://github.com/stevenhoneyman/wpa_gui/tree/master/wpa_supplicant-2.4
Description: Multiple buffer overflows in kernel in Intel Manageability Engine Firmware 11.0/11.5/11.6/11.7/11.10/11.20 allow attacker with local access to the system to execute arbitrary code. Impact: Local attackers can exploit these issues to execute arbitrary code in the context of the affected application. Failed exploit attempts will likely result in denial-of-service conditions. Intel Manageability Engine versions 11.0, 11.5, 11.6, 11.7, 11.10, and 11.20 are vulnerable. Mitigation:...
Read More
Description: Microsoft Office 2010, SharePoint Enterprise Server 2010, SharePoint Server 2010, Web Applications, Office Web Apps Server 2010 and 2013, Word Viewer, Word 2007, 2010, 2013 and 2016, Word Automation Services, and Office Online Server allow remote code execution when the software fails to properly handle objects in memory. Impact: An attacker can leverage this issue to execute arbitrary code in the context of the...
Read More
Description: Microsoft Office 2016 Click-to-Run (C2R) and Microsoft Office 2016 for Mac allow an attacker to use a specially crafted file to perform actions in the security context of the current user, due to how Microsoft Office handles files in memory, aka “Microsoft Office Remote Code Execution Vulnerability”. Impact: An attacker can leverage this issue to execute arbitrary code in the context of the currently...
Read More
October’s macOS security update contained a fix for a vulnerability that Trend Micro privately disclosed to Apple earlier this year. The vulnerability (designated as CVE-2017-13811), was in the fsck_msdos system tool. This tool checks for and fixes errors in devices formatted with the FAT filesystem, and is automatically invoked by macOS when a device using FAT (such as a USB disk or an SD card) is inserted. The vulnerability...
Read More