licious cyber actors continue to exploit known vulnerabilities and use publicly available tools to target networks of interest. Remote code execution (RCE) attacks allow an attacker to remotely execute malicious code on a computer. The impact of an RCE vulnerability can range from malware execution to an attacker gaining full control over a compromised machine. RCE vulnerabilities are some of the most risky and high-impact...
Read More
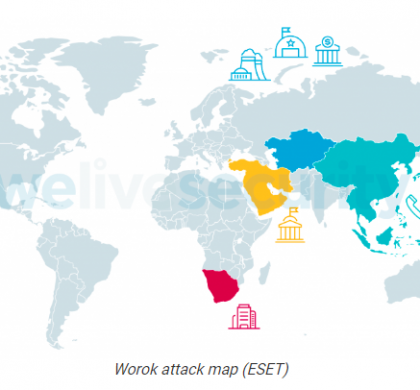
A new cyber espionage threat group that has been previously unknown named Worok and has been observed using undocumented tools targeting private and local government entities mostly in Asia. Based on the report by ESET, the group has been active for at least 2020 and observed a significant break in operation from 2021-05 to 2022-01, but in 2022-02, their operation resumed, targeting an energy company, and a public...
Read More
An authentication bypass using an alternate path or channel vulnerability [CWE-288] in FortiOS, FortiProxy and FortiSwitchManager may allow an unauthenticated atttacker to perform operations on the administrative interface via specially crafted HTTP or HTTPS requests. Exploitation Status: Fortinet recommends immediately validating systems against the following indicator of compromise in the device’s logs:user=”Local_Process_Access” Affected ProductsFortiOS version 7.2.0 through 7.2.1FortiOS version 7.0.0 through 7.0.6FortiProxy version 7.2.0FortiProxy version...
Read More
The tech giant has uncovered more than 400 malicious Android and iOS apps this year which steal usernames and passwords. 45 out of the 400 apps it found were on iOS, while the rest were on Android. They masquerade themselves as popular services like photo editors, games and VPNs to trick people into downloading them. How do these malicious apps work? Apart from displaying fun...
Read More
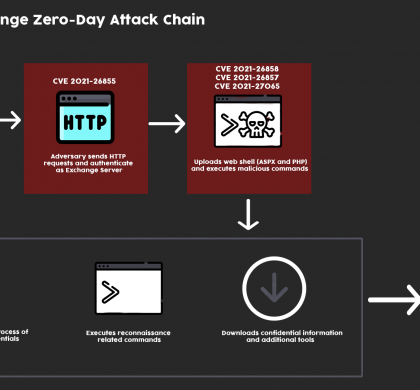
Microsoft has confirmed that two reported zero-day vulnerabilities in Microsoft Exchange Server 2013, 2016, and 2019. The first one, identified as CVE-2022-41040, is a Server-Side Request Forgery (SSRF) vulnerability, and the second one, identified as CVE-2022-41082, allows Remote Code Execution (RCE) when PowerShell is accessible to the attacker. From the note Microsoft added, CVE-2022-41040 can enable an authenticated attacker to remotely trigger CVE-2022-41082. It should...
Read More