Exchange vulnerabilities CVE-2022-41040 and CVE-2022-41082
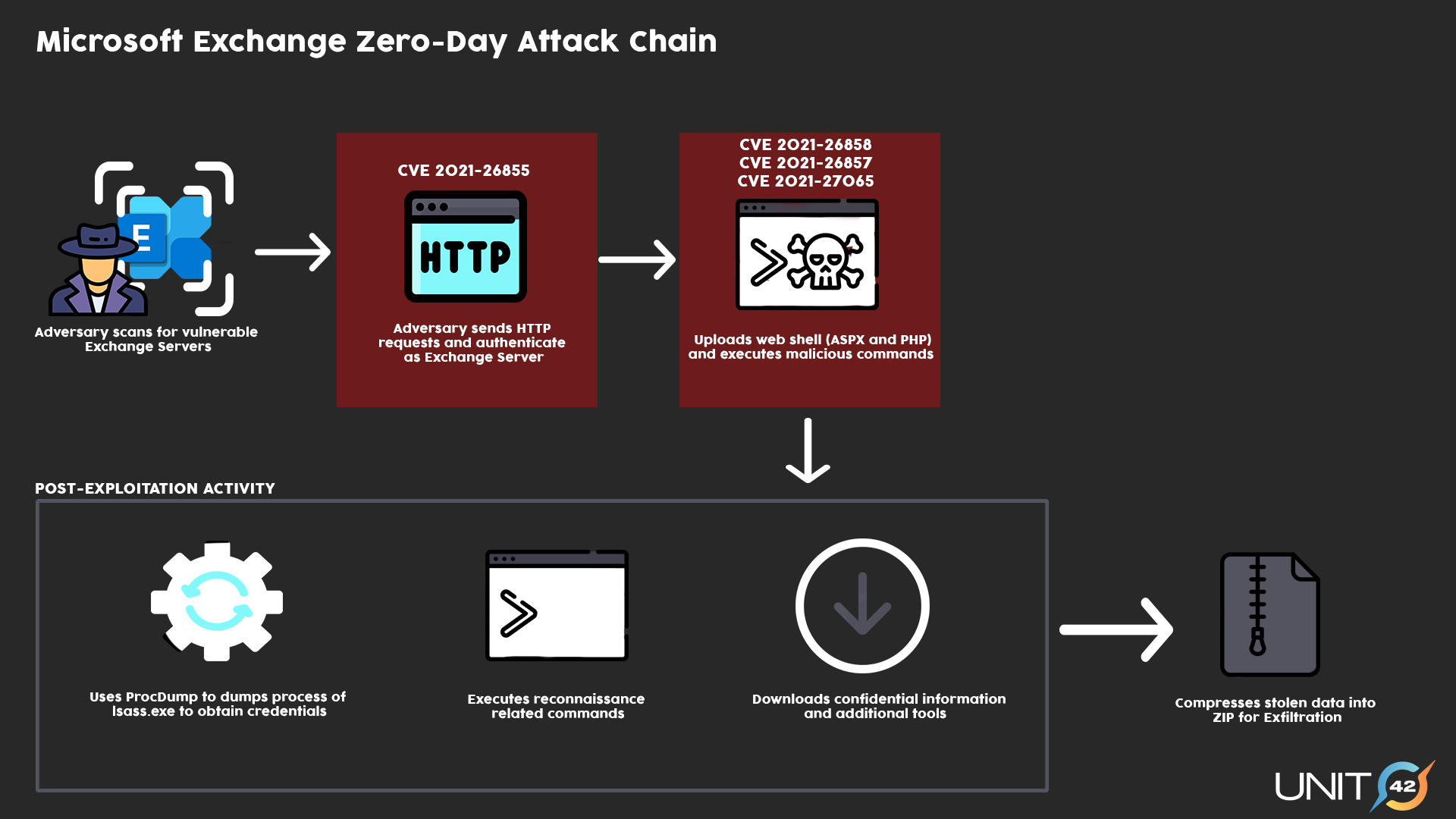
Microsoft has confirmed that two reported zero-day vulnerabilities in Microsoft Exchange Server 2013, 2016, and 2019. The first one, identified as CVE-2022-41040, is a Server-Side Request Forgery (SSRF) vulnerability, and the second one, identified as CVE-2022-41082, allows Remote Code Execution (RCE) when PowerShell is accessible to the attacker.
From the note Microsoft added, CVE-2022-41040 can enable an authenticated attacker to remotely trigger CVE-2022-41082. It should be noted that authenticated access to the vulnerable Exchange Server is necessary to successfully exploit either vulnerability.
Mitigation:
Exchange Online customers do not need to take any action.
Exchange Server user should review and choose only one of the following three mitigation options.
Option 1: For user who have the Exchange Server Emergency Mitigation Service (EMS) enabled, Microsoft released the URL Rewrite mitigation for Exchange Server 2016 and Exchange Server 2019. The mitigation will be enabled automatically. Please see this blog post (https://techcommunity.microsoft.com/t5/exchange-team-blog/new-security-feature-in-september-2021-cumulative-update-for/ba-p/2783155)for more information on this service and how to check active mitigations.
Option 2: Microsoft created the following script for the URL Rewrite mitigation steps. https://aka.ms/EOMTv2
Option 3:
Open the IIS Manager.
Expand the Default Web Site.
Select Autodiscover.
In the Feature View, click URL Rewrite.
In the Actions pane on the right-hand side, click Add Rules.
Select Request Blocking and click OK.
Add String “.autodiscover.json.\@.Powershell.” (excluding quotes) and click OK.
Expand the rule and select the rule with the Pattern “.autodiscover.json.\@.Powershell.” and click Edit under Conditions.
Change the condition input from {URL} to {REQUEST_URI}
For more details please visit Reference URL.
Reference:
https://msrc-blog.microsoft.com/2022/09/29/customer-guidance-for-reported-zero-day-vulnerabilities-in-microsoft-exchange-server/
https://www.microsoft.com/security/blog/2022/09/30/analyzing-attacks-using-the-exchange-vulnerabilities-cve-2022-41040-and-cve-2022-41082/
https://microsoft.github.io/CSS-Exchange/Security/EOMTv2/
https://www.bleepingcomputer.com/news/microsoft/microsoft-confirms-new-exchange-zero-days-are-used-in-attacks/











