Operation Tripoli
by CIRT Team
A large-scale campaign has been distributing malware on Facebook for an unspecified number of years primarily targeting the country of Libya, according to Check Point researchers. The threat actors behind this campaign are utilizing the geopolitical and political pages themed around Libya that attempt to convince individuals to download malicious files. Researchers identified more than 30 Facebook pages distributing malicious links and some of the pages were found to have more than 100,000 followers. The objective of this campaign is to distribute malicious links and files, some of which are stored in services like Google Drive, or divert traffic to a compromised websites hosting the malicious files, infect a user, and steal sensitive information
In
the Name of Haftar
The Facebook page impersonating Khalifa Haftar was created at the beginning of April 2019, and has since managed to recruit more than 11,000 followers. The page shares posts which have political themes, and include URLs to download files marketed as leaks from Libya’s intelligence units. The description in the posts claims that those leaks contain documents exposing countries such as Qatar or Turkey conspiring against Libya, or photos of a captured pilot that tried to bomb the capital city of Tripoli. But instead of the promised content in the posts, the links would download malicious VBE or WSF files for Windows environments, and APK files for Android. The threat actor opted for open source tools instead of developing their own, and infected the victims with known remote administration tools (RATs) such as Houdini, Remcos, and SpyNote, which are often used in run-of-the-mill attacks. In our case, the malicious samples would usually be stored in file hosting services such as Google Drive, Dropbox, Box and more.
A Wide Network of Facebook Pages
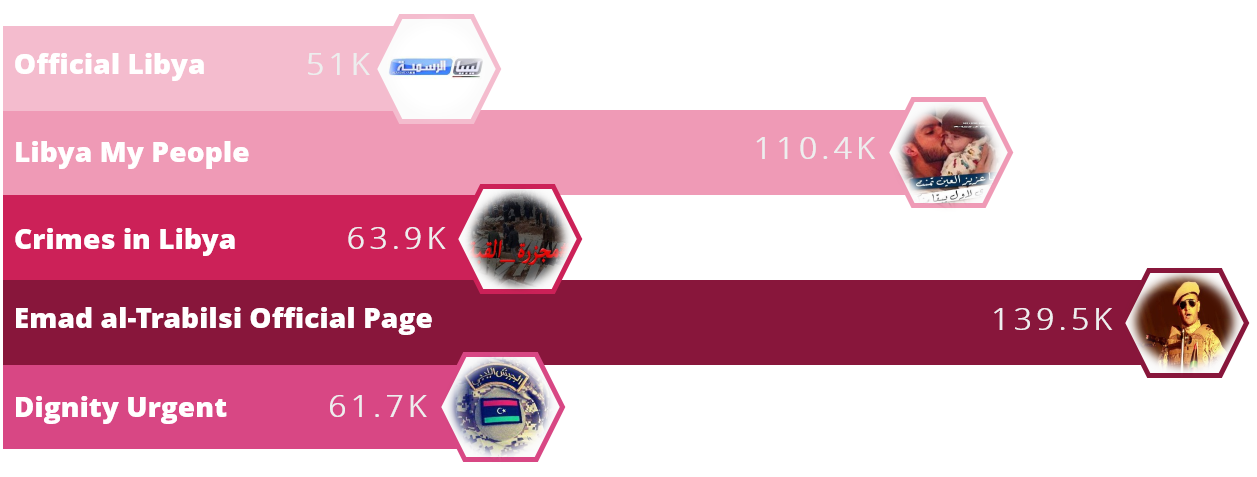
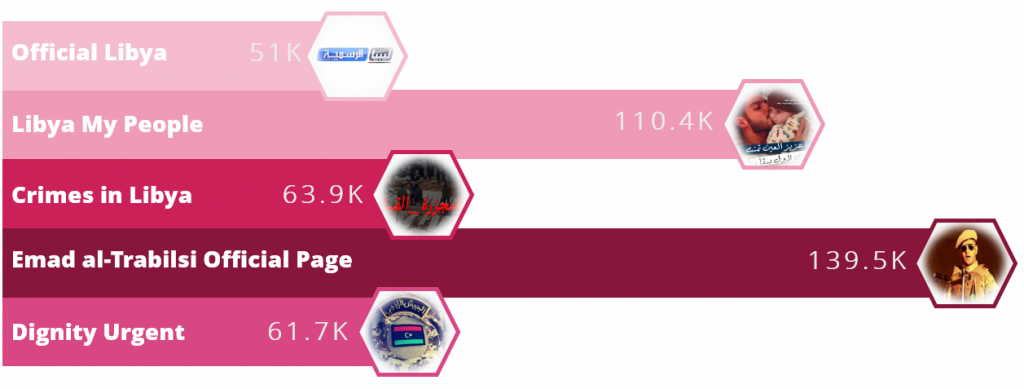
By looking up the unique mistakes, we were able to find more than 30 Facebook pages that have been spreading malicious links since at least 2014. Some of those pages are extremely popular, have been active for many years, and are followed by more than 100K users. Below are the five most popular Facebook pages that used in this attack, and the amount of followers each one has:
Looking at the activity over the years, it seems that the threat actor gained access to some of the pages after they were created and operated by the original owners for a while (perhaps by compromising a device belonging to one of the administrators).
The pages deal with different topics but the one thing they have in common is the target audience that they seem to be after: Libyans. Some of the pages impersonate important Libyan figures and leaders, others are supportive of certain political campaigns or military operations in the country, and the majority are news pages from cities such as Tripoli or Benghazi.
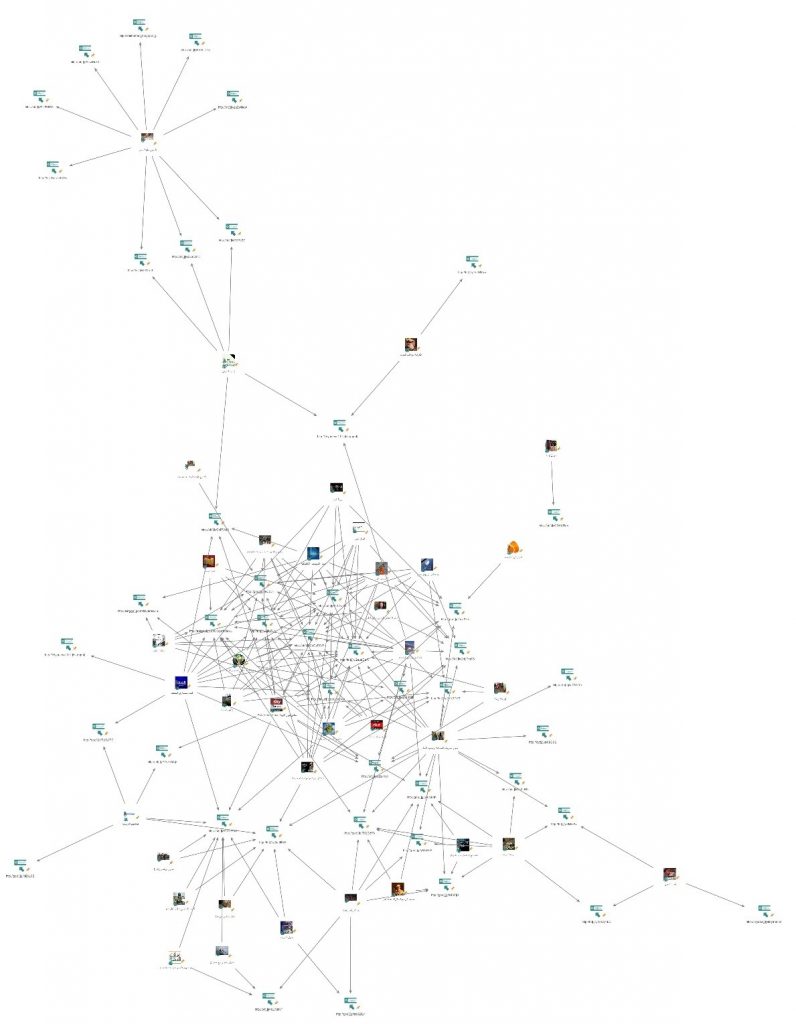
In total, there are more than 40 unique malicious links used by the attacker over the years, which were shared in those pages. When visualizing the connections between the pages and the URLs used in different phases of this operation, we found that the malicious activity was highly intertwined as many of the links were spread by more than one page:
Recommendation: This story is
an example of social engineering tactics threat actors use to trick users into
installing malware on their machines. All social media users should be cautious
when accepting unknown user requests, and particularly cautious when receiving
communication from unknown users. Even if callers state they are from the bank
or another trusted entity, it is best practice to avoid giving any details over
the phone and not access unknown websites that are given by the callers. If you
are unsure about the legitimacy regarding security modules, contact your bank
directly and ask, as well as speak to management to ensure that updates are
necessary and genuine.










