Traditional VAPT VS Effective Security Testing & Assessment Program For Enterprises

by CIRT Team
“Cybersecurity Professionals Need To Win Every Time, But An Attacker Only Need To Win Once!!!”
Now a days VAPT becomes more essential tasks required for the organizations to keep their Cyber/ IT enabled Information Systems secure against the ongoing cyber threats. Performing VAPT is also treated as mandatory requirement by some compliances like as PCI-DSS.
Gaps in traditional VAPT
“Cost of an Exploitation Always Much Higher Than Cost Of Effective Security Testing!”
- In most cases VAPT is driven by the compliance and regulatory requirements rather than focusing (ensure/ enhancing) the security and safety of the organization’s cyber space.
- Till now in our country, most organization don’t have independent information security dept. or team, whereas security team is formed within IT dept. and due to lack of effective Information Security governance and conflict of interest, IT Security team can’t enforce other adjacent teams regarding the detected/ unpatched vulnerabilities.
- As always business dominates the organization, by nature business team always try to deny the update/ change due to any vulnerability by showing business losses (whereas they even don’t have interest to realize the aftermath of an incident due to such vulnerabilities.)
- In some organization, VAPT within a network exercise only focused to the servers, hosts or endpoint devices where they ignore network devices (Router, Switches, Firewalls etc.) from the scope, which also may vulnerable and crucial to make the perimeter secure.
- Unfortunately, without realizing the cost of a breach, Pentest/ Red team assessment assumes costly in our industry.
- Proper knowledge regarding the red team/ pen-test engagement processes, tools, techniques, exploitation as-well-as the purpose and expected outcome from such security testing.
- In some cases, 3rd party vendors or service providers may have intention to reduce the workforce to discover and exploit vulnerability with deep-drive, due to feasibilities of timeframe, unskilled resources or any other issues.
- Finally, shortage of experts in our industry.
Why need effective exploitation of vulnerabilities through security testing?
“Before anyone exploit you, it’s better to exploited by own to!”
Though everyone knows that vulnerable service or products are needed to avoid and replace/ update by considering the organization’s safety, but end of the day some people also thinks that hackers can’t find their vulnerabilities and they are not in such danger. This is also considerable that, system/ asset owners are always passing busy time to keep the service up with no interruption.
“100% Service Uptime Without Secure Measures Lead to Such Situations!!”

Fig: [Ref: https://www.mediagistic.com/blog/the-leaky-bucket-syndrome-are-you-set-up-to-handle-inbound-web-leads]
“Continuous Patching & Updating/ Upgrading The Systems Or Assets In Timely Fashion Is Really A Boring Tasks, And We Always Love To Lead A Hassle-Free Work!!!”
So, effective security testing and assessments may helpful:
- To draw a clear picture of remaining vulnerabilities and risk factors to the organization’s assets.
- To defend against our de-motivation of keeping the systems up-to-date, successful exploitation of vulnerabilities to show the level of security posture through effective security testing and assessment is necessary.
- Such exploitation may effective to make conscious all of stakeholders to keep their systems/ assets up-to-date from the released vulnerabilities.
- To ensures whether suitable security policies are being followed or not
Effective security assessment and vulnerability management program
This is recommended to initiate and maintain an organization wide security testing and vulnerability management program to better adherence of the security culture among the all entities to the organization. An effective vulnerability management program may include:
- Define the Testing scopes and assessment criteria along with definition of terms and conditions.
- Security Testing of all the assets and applications.
- Remediate and resolve the detected vulnerabilities.
- Final Report submission along with observation and recommendations.
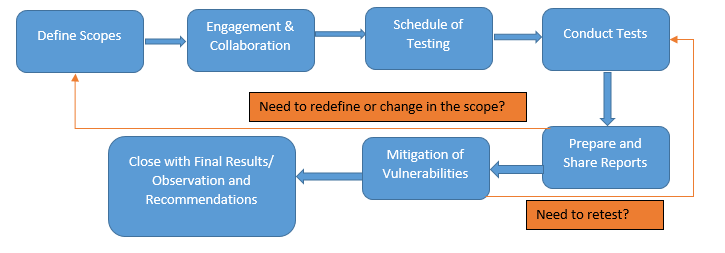
Fig: Typical Security Testing workflow
Scoping for the security testing:
- Define the scope of pen-test or Red Team wisely and consider to coverage of most of the assets within the whole network (without considering only PCI DSS, SWIFT or ISO zones or networks), as we should consider that security is required for organization’s safety not only for compliance.
- Don’t rigid the scope within defined lists of assets, also encourage teams to discover and test the hidden or chain vulnerable assets (discovered during the pen-test) and adjust these in final VAPT scope.
- Include fire-walking, network segmentation test and FW Ruleset review to check the effectiveness of Firewalls and zone configurations. Also include network devices in VAPT checklists to identify and patch-up vulnerabilities in timely manner.
- Regularly test the web based and other application in regards to OWASP top 10 and other well-known application and API related vulnerabilities (APIs are currently focused as one of the top attack vectors).
- Always think twice before finally declare the scope of assessment and rule of engagements.
- Some considerable tasks may define in scope of security testing:
- Vulnerability Scanning & Penetration Testing of all Servers, Network Devices and Databases
- Testing of all Application Servers resided in the DMZ, DNS, Proxy servers.
- Testing of web applications including all e-commerce portals, PG and all other public facing systems.
- Fire-walking, Firewall rulesets review, Network Segmentation Tests
- Rogue wireless AP detection tests (Wireless scanning)
- Check for unauthorized physical access control within the secure areas
- And many more!!!
Scheduling of assessments/ tests:
To get effective outcome from security assessment and testing this is recommended to prepare a plan and feasible schedule by considering the scope and timeframe. An appropriate testing schedule may help organizations:
- To keep proper track of the assets and or applications, to which testing is performed and vulnerabilities are mitigated.
- To trace Gaps in testing scopes
- To meet the compliance requirements as-well-as keep the systems up-to-date from ongoing vulnerabilities
- To define annual forecast as tasks for the security testing teams
A typical schedule for the tasks associated with security testing and assessments is defined here, which illustrates how an Information Security Team can define the network segments and other applications as-well-as tasks for Pen-Testing/ Red Team Assessments.
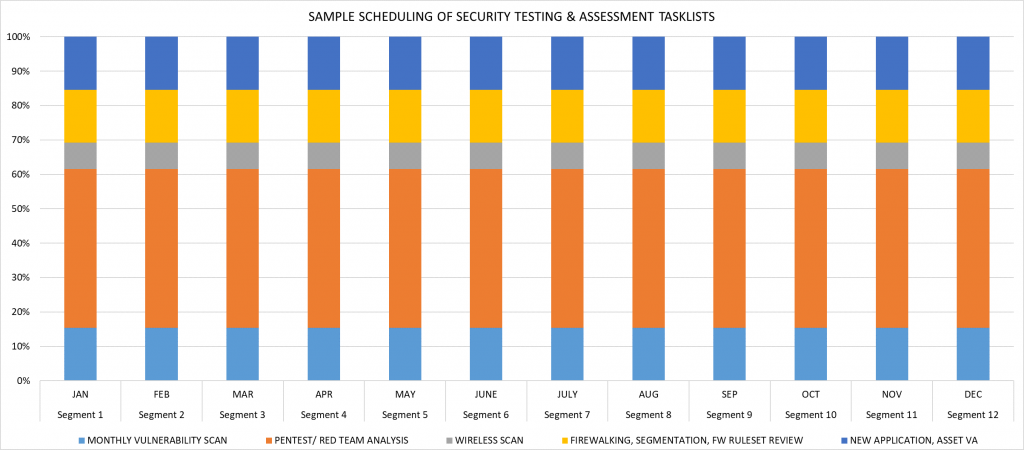
Fig: Sample Projection of Yearly Security Testing and Assessments
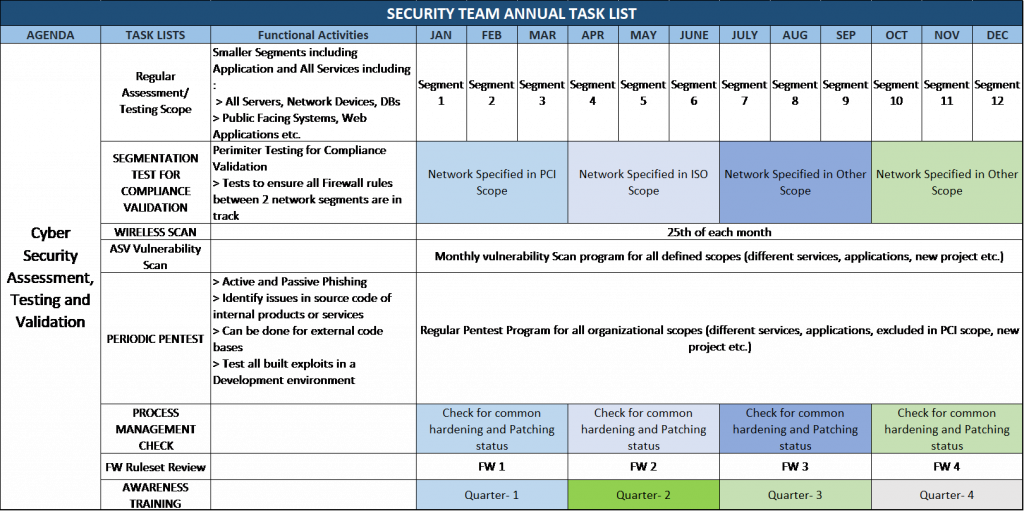
Fig: Sample Annual Security Assessment and Testing Related Task Lists and Scheduling
Considerable Assessment Feasibility:
- Security tester should be free to discover residing vulnerabilities by considering the avoiding of interruption of services.
- If any test has possibilities to disrupt the services, then security tester should inform relevant administrator or entity regarding the test and choose a suitable time to perform such tests.
- Tester should follow the declared timeline to test the specific assets or application as prescheduled manner.
- Security tester should have encouraged to discover the hidden vulnerabilities or 0-days by assessing the codes or asset configurations with deep-drive (not only look for the detected vulnerabilities by the automated vulnerability scanner).
- Security tester or 3rd party service provider must conduct a NDA along with rules of engagements regarding the disclosure of detected and exploited vulnerabilities prior to perform any security testing.
- Security tester may have freedom to choose tools and techniques preferred by them, but to conduct vulnerability scan for any specific compliance they should use compliance validated scanner (like as for PCI DSS compliance this is mandatory to use any ASV scanner for vulnerability scanning.)
Qualities for a qualified Security Assessor/ Tester:
- Clearly understand the scope of work, assets within the scope, restrictions, allowed methods, tools or techniques.
- Critical and off-the-box thinking and hacker approach
- Choose a suitable set of tests as-well-as tools that balance cost and benefits
- Follow suitable procedures, standards and techniques with proper planning, documentation and evidences (PoCs).
- Establish the scope for each penetration tests, such as objective, limitations and justification of procedures.
- Be ready to show how to exploit the vulnerabilities also regeneration of exploitation if needed.
- State the potential risks along with risk ranking, possible threat sources and other findings in the report.
- Provide suggestions and references for feasible and possible methods to mitigate the vulnerabilities and associated risks.
- Keep themselves updated at all times as technologies are advancing rapidly.
Remediation of Vulnerabilities:
Though, this is recommended to remediate all the detected vulnerabilities within shortest period of detection, but in practical some vulnerabilities are not possible to patch-up ASAP due to dependency of release patches from the vendors or any other dependencies. In such scenarios:
- Rather than counting vulnerable IP addresses, consider counting total number of unique vulnerabilities and efforts to remediate vulnerabilities (counting of IP addresses may seems bigger than the number of unique vulnerabilities!)
- Administrators or asset/ application owner should prepare a detail plan for the feasible remediation of vulnerabilities.
- Deploy the compensating control to uncovered vulnerabilities
- Should prepare a risk acceptance by defining/ demonstrating the proper difficulties, reasoning and dependencies.
RED TEAM Exercise
A thorough Red Team exercise will test and expose vulnerabilities in a multitude od areas, whereas typical VAPT focuses to exploitation of technical or IT Assets and operation is limited to IT enabled systems. Typically, Red Team operation focuses on:
- Technologies: Networks, applications, routers, switches, databases, appliances etc.
- People: Staffs, contractors/ vendors, departments, business partners, supply chains etc.
- Physical: Office areas, buildings, warehouses, substations, data centers, power facilities etc.
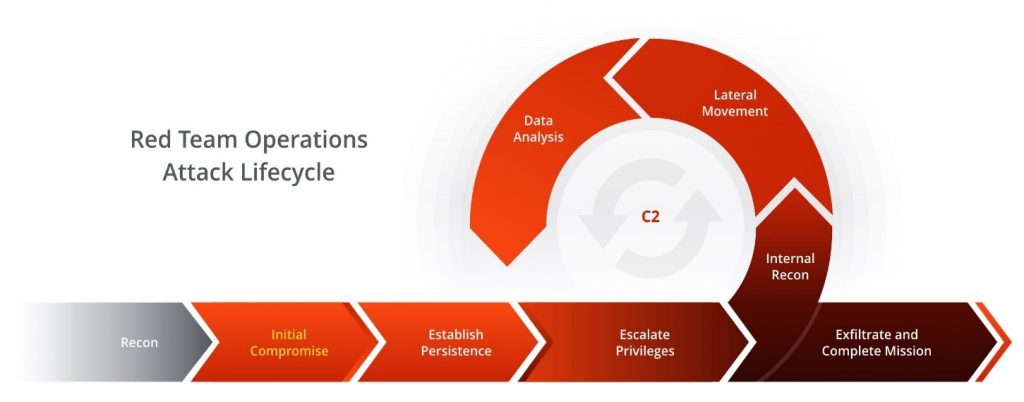
Fig: RED TEAM Assessment Cycle [Ref: https://sera-brynn.com/understanding-the-red-team-cycle/]
For the large organizations having lots of IT assets, application and also affordable to having dedicated team to detect vulnerable and stealthy points within the organization as-well-as organization’s assets/ applications, this is recommended to exercise RED Team assessments to discover and exploit the weakest links to the enterprises. Red Team assessments may provide:
- Simulation of Internal & External attacks and tests the organization’s response strategy and accuracy to the threats.
- Actual security posture within the organization by initiating real life attack scenarios like as social engineering, phishing and other technique.
- An overview of how the systems secure and responds to any attacks in regards to C2C communication establishment and persistence to the network.
- An assessment result on the physical security strength and access control effectiveness within the organization.
- Finally, understanding of the defense mechanism as-well-as offences and in a more realistic understanding of risk associated to the organization.
References
- NIST SP 800-115 (https://csrc.nist.gov/publications/detail/sp/800-115/final)
- PCI Penetration Testing Guidance: v-1.1 (https://www.pcisecuritystandards.org/documents/Penetration-Testing-Guidance-v1_1.pdf?agreement=true&time=1602570272621)
- PTES (http://www.pentest-standard.org/index.php/Main_Page)
- OWASP Testing Guide v5
Md. Makchudul Alam
Incident Handler
BGD e-GOV CIRT










