Role Based Access Control (RBAC) in Elastic Stack
by CIRT Team
We are all familiar with the Elastic Stack for various purposes. Today, I will let you know about a feature which was previously paid one, but in Elastic Stack 7.0 it has been made free.
Role based access control is a feature which will allow users to have permission in specific domain only. This is a must need for a large environment where there are several users with different purposes who has access to the same Elastic Stack instance. This is attained by enabling the Xpack Security feature in Elastic Stack.
The first thing which is required to implement role based access control is to install SSL/TLS in Elasticsearch and all the components which have access to the Elasticsearch instance. If anyone uses Logstash to transform data, then Filebeat doesn’t need to have SSL/TLS enabled. In this scenario only Elasticsearch, Logstash and Kibana must have SSL enabled. The steps to enable SSL/TLS is explained below.
- First we have to generate the CA certificate which will be used in every hosts which need to have SSL enables. All the certificates need to be locally present in each host. CA certificate location must be used in the parameter elasticsearch.ssl.certificateAuthorities
- Then we need to generate the server.ssl.certificate and server.ssl.key for all of the required hosts. Let’s assume we have a deployment of 03 ElasticSearch nodes, 02 Logstash nodes and 01 Kibana node. We will have to create certificate and key for all of these 06 Hosts. This can be done from one single ElasticSearch node and can be distributed to other nodes.
- After the certificate is generated and distributed to all of the respective node along with CA certificate, we will have to modify the configuration file for ElasticSearch, Logstash and Kibana.
- First of all, xpack.security.enabled must be set to true. Next, give the proper location of the respective files for elasticsearch.ssl.certificateAuthorities, server.ssl.certificate and server.ssl.key. Also the elasticsearch.ssl.verificationMode should be set to certificate to make this work properly.
- Some default users are created when setting up SSL which will be used for authenticating Logstash and Kibana to Elasticsearch. We also need to create one additional user which will be used to send the logs to Elasticsearch from logstsash.
- Finally, we have to restart the services to make the changes to take effect.
Upon login to Kibana using the admin password created in the previous steps, we will now see a new option in the Management window namely Security which was not present before. In Security, there are three options which are Users, Roles and API.
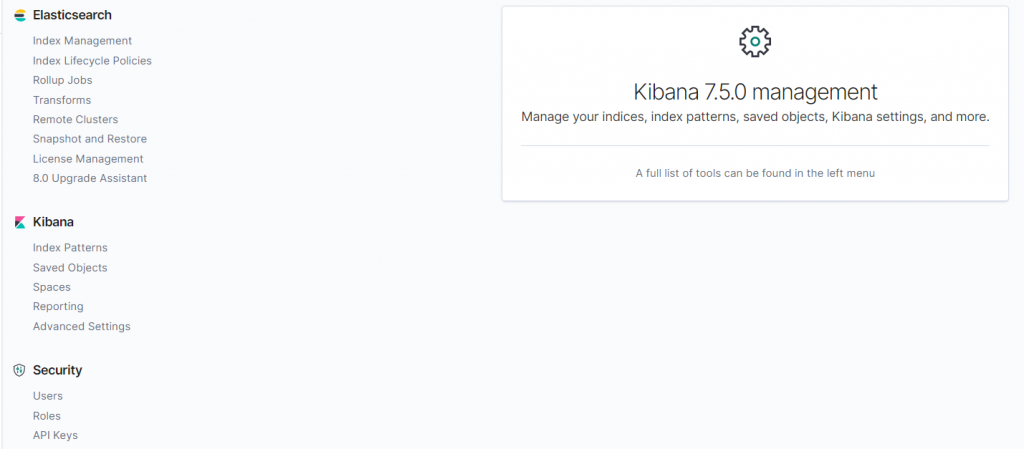
- In the Users tab, we can create new users, assign roles and modify them accordingly.
- In the Roles tab, we can create specific roles having the given privileges to them in the Elasticsearch (Cluster, Indices) and Kibana (Spaces). This role is then assigned to the users to have specified permissions in the Elastic Stack.
- In the API keys tab, user can create API key to access the Elasticsearch without requiring basic authentication. This can be created from the console as there is no GUI option for this.
So, this is the Role Based Access Control (RBAC) for Elasticsearch and here is my two cents on implementing it.
———————————————————-
Sumit Kumar Pramanik
BGD e-GOV CIRT, Data Center Hardware Engineer









