Google Fixes Serious Security Bug Impacting Gmail, G Suite Users
by CIRT Team
Google has patched a major security bug impacting the Gmail and G Suite email servers. The bug could have allowed a threat actor to send spoofed emails mimicking any Gmail or G Suite customer. The issue was identified and reported to Google in April, though the search giant took over four months in mitigation and ultimately released a patch on Wednesday (19th August).
According to security researcher Allison Husain, who found and reported this issue to Google in April, the bug also allowed attackers to pass the spoofed emails as compliant with SPF (Sender Policy Framework) and DMARC (Domain-based Message Authentication, Reporting, and Conformance), two of the most advanced email security standards. As for the bug itself, the issue is actually a combination of two factors, as Husain explains in her blog post.
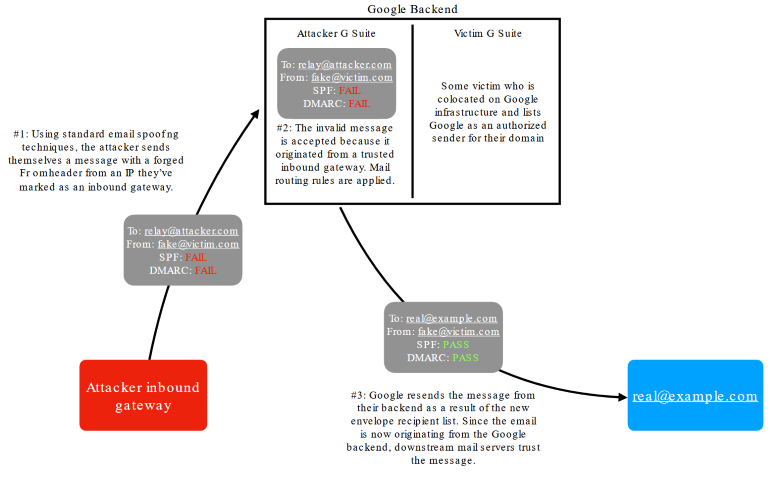
The first is a bug that lets an attacker send spoofed emails to an email gateway on the Gmail and G Suite backend.
The attacker can run/rent a malicious email server on the Gmail and G Suite backend, allow this email through, and then use the second bug.
This second bug allows the attacker to set up custom email routing rules that take an incoming email and forward it, while also spoofing the identity of any Gmail or G Suite customer using a native Gmail/G Suite feature named “Change envelope recipient.”
The benefit of using this feature for forwarding emails is that Gmail/G Suite also validates the spoofed forwarded email against SPF and DMARC security standards, helping attackers authenticate the spoofed message. See Husain’s graph below for a breakdown of how the two bugs can be combined.

Image by Allison Husain
“Additionally, since the message is originating from Google’s backend, it is also likely that the message will have a lower spam score and so should be filtered less often,” Husain said, while also pointing out that the two bugs are unique to Google only.
If the bug had been left unpatched, no doubt that the exploit would have most likely been widely adopted by email spam groups, BEC scammers, and malware distributors.
Google’s mitigations have been deployed server-side, which means Gmail and G Suite customers don’t need to do anything.
Reference:









