Fileless Malware: An Emerging Threat

by CIRT Team
- Introduction
Fileless malware attack is on the rise, and it’s one of the foremost important digital infiltration threats to companies, according to Symantec’s 2019 Internet Security Threat Report. The magnitude of this threat is usually seen within the Report’s finding that malicious PowerShell scripts — one of the key components of fileless malware attacks — increased quite 1,000 percent in 2018 and accounted for 89 percent of fileless malware attacks [1]. As of carbon black recently interviewed over 400 security researchers who discussed non-malware attacks, AI (AI) and machine learning (ML), among other topics. supported this, 64 percent said that their companies are experiencing an increasing number of fileless malware attacks, 93 percent consider fileless malware attacks more threatening than traditional malware and 62 percent of fileless malware attacks target customer data.[2]
As of carbon black report, utmost common sorts of fileless attacks were:
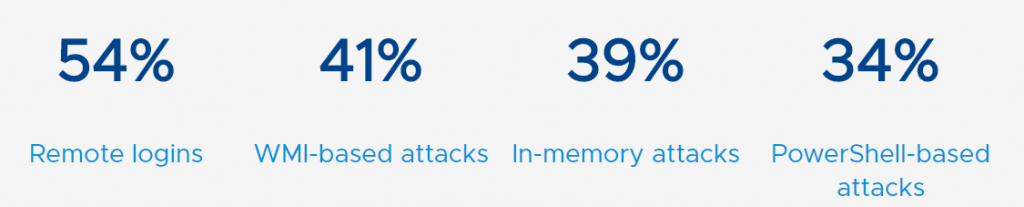
Figure 1.1: Statistics of Different type of Fileless Malware Attack. Image Source: VMware Carbon Black
In addition to going after customer data, fileless malware attacks mostly targeted corporate IP (53%), credentials (42%), and financial data (41%). Over half fileless malware attacks were designed for service disruption.[1]
- Categorization of Fileless Attack
To demystify the term, the Microsoft Defender threat analysis team started categorising fileless attacks based on how they get onto a PC and where they’re hosted. There are more than a dozen combinations of those ‘entry points’ and malware hosts getting used for fileless attacks — a number of that are very sophisticated and are seldom used for targeted attacks, and a few of that have been commoditised and are showing up more often for common attacks like making an attempt to run a coin miner on the system. However, they constitute three broad groups.
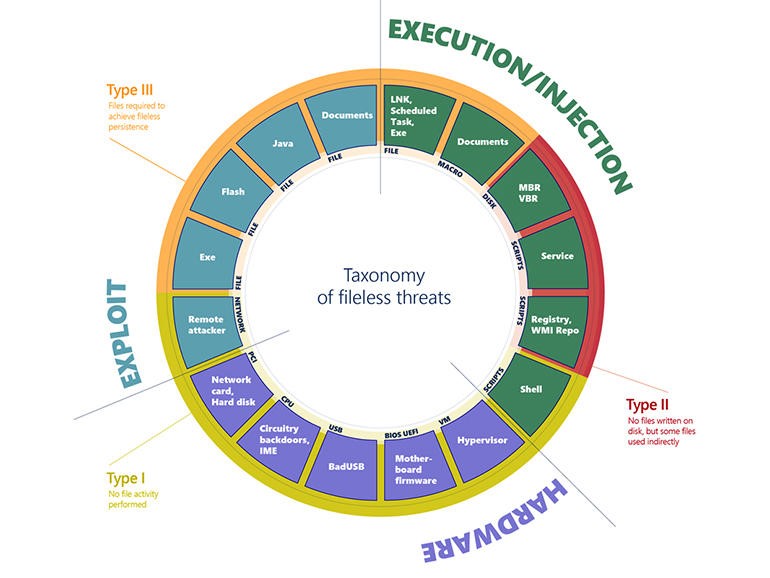
Figure 2.1: Categorization of Fileless Attack. Image
Source: Microsoft
Type one is really fileless, during which the attack is delivered on the network or from a device, the payload is handled in memory and nearly naught touches the disk at all. For instance, EternalBlue is a cyberattack exploit developed by the U.S. National Security Agency (NSA) and was leaked by the Shadow Brokers hacker group on April 14, 2017, one month when Microsoft released patches for the vulnerability. These are truly the most advanced attacks out there, but most of the attacks that get called fileless don’t belong in this group.
Type two attacks do use files, but indirectly, in order that they still count as fileless. Think of scripts getting used to launch attacks, whether it’s JavaScript or PowerShell. We see a couple of that focus on the MBR and check out to render machines completely useless in order that they won’t boot. But they mostly use the registry and WMI and various other mechanisms like PowerShell to leverage a number of the tools that are already present on the system to sequence setup activities.
Type three clearly begin with a file whether it is a document file with a macro in it, or a Java file, or Flash file, and sometimes even EXE files that drop certain files, however then persistence is fileless. So as soon as the payload is dropped, the payload achieves persistence through both staying simply in memory or staying in the registry and running from there.
Many of these Type three attacks come from email, but the file attachments won’t show up as obviously malicious if an antivirus scans the files. Generally, .EXE file isn’t attached in email rather a document is attached with a macro which links to a different file then that file goes and downloads the payload. VBA code doesn’t have a binary that antivirus software can scan, but it can load PowerShell scripts that download and run attacks.
- What Is Fileless Malware
Fileless malware does not leverage traditional executable files like as file base malware does. It uses a way called living-off-the-land binaries — or “LoLBins”. Living-off-the-land tactics mean that attackers use legitimate tools for malicious purposes. There are more than 100 Windows system tools that can be leveraged and abused as LOLBins such as PowerShell, Windows Management Instrumentation (WMI), .NET Framework, Microsoft Office Macros. It piggybacks on legitimate scripts by executing malicious activity while the legitimate programs still run. Moreover, it can remain undetected because it’s memory-based, not file-based. Instead, the fileless malware is written on to the RAM and does its deed from the memory. It remains there, causing problem, until the computer is rebooted. Antivirus software often works with other sorts of malware because it detects the normal “footprints” of a signature. As fileless malware leaves no footprints therefore antivirus products can not detect.
- How Fileless Malware Work
As mentioned, fileless malware is not hooked in to files being downloaded, installed and executed. It uses a far sneakier method of infecting a computer and executing, hiding within legitimate software packages, user tools and applications that already are installed on the pc . After analyzing such threats researchers have revealed numerous ways attackers use to infect victims. Some are traditional, others not so traditional.
The following are a few of the way been seen within the past exploited by attackers:
Phishing emails that include malicious downloads and links: With this method, the bulk of malware found is installed on the disk drive. However, fileless ransomware, codes are often remotely executed from memory or when a script is executed.
Legitimate applications: Compromised software packages installed like Word and JavaScript are often hijacked by attackers to execute malware.
Native application: Operating systems come with a number of preinstalled tools, like PowerShell and Windows Management Instrumentation (WMI), which can be exploited by attackers to run malicious code while piggybacking with legitimate code.
Lateral infection: By abusing PowerShell, certain fileless variants are seen moving laterally across networks, infecting other computers on an equivalent network.
Malicious websites masquerading as legitimate websites: An attacker will create a website to appear almost exactly like a legitimate business. When a user visits the website, in the background the website scans for vulnerabilities in plugins which might allow malicious code to be run within the browser’s memory.

Figure 3.1: How Fileless Malware work. Image Source: CSO online
For Example, as can be seen from Figure 3.1 the steps of how fileless malware are targeting PowerShell as abuse LOLbins.[3]
Step 1: User receives a phishing email with a link to a malicious website.
Step 2: User clicks on the link.
Step 3: The malicious website loads Flash, which has known vulnerabilities on the user’s computer.
Step 4: Flash opens the Windows PowerShell tool, which can execute instructions through the command line while operating in memory.
Step 5: PowerShell downloads and executes a script from a command and control server.
Step 6: The PowerShell scripts locates and sends the user’s data to the attacker.
- Fileless Malware Mitigation
As nothing is normally written to a computer’s hard disk during an fileless malware attack, standard, signature-based antivirus programs are normally ineffective. So, what is the best way to mitigate against this attack if, on the surface they appear to be executing legitimate computer instructions. The simplest way to avoid the upload of this type of malware is to avoid clicking on the links that install the malicious code. Of course, this is not always possible, particularly when this malware is uploaded from legitimate-looking websites. Furthermore, hackers are often adept at redirecting their targets to illegitimate web locations that are virtual copies of legal websites.
However, there are other, more practical measures that companies and consumers can go for avoid painful fileless malware attacks.
These include the following:
- Do patching operating systems as often as recommended by manufacturers.
- Deploying a process of “least privilege” and PowerShell logging
- Instituting systematic network behavior analysis including the monitoring of computer process logging for unfamiliar activity.
- Disabling unnecessary macros in Windows programs such as Excel, PowerPoint, and Word.
- Computer service monitoring to identify any unusual service creation on regular basis.
As fileless malware attack is difficult to detect using standard antivirus packages and it is hard to remove even if it is located, multi-level security provides a robust method of defending against memory-resident
malware. This approach is increasingly deployed due to the expansion of corporate network perimeters as the growing use of mobile, IoT, and cloud technology make traditional antivirus protection ineffective. Multi-layer defense involves applying security measures across all of an enterprise’s technology platforms. For instance, the smartphone layer would consist of the following security measures:
- Prevent modified operating systems from booting
- Kernel integrity monitoring
- Isolated execution of co-processors
- Drive encryption
- Secure storage
Similar defenses should be established across other layers of an organization’s technology infrastructure to include:
- Firewall management
- Email protection
- Web gateways
- Micro data segmentation
In addition to going multi-layer, enterprises must also get predictive. Potential fileless malware attacks can be mitigated by monitoring suspicious network behavior. For instance, configuring IP numbers to extract those emanating from unusual or irregular geographical areas can flag those connections and potentially block access.
Artificial intelligence (AI) systems are probably the way that subsequent generation of antivirus programs will develop within the future. AI can recognize “normal” network behavior and determine if anomalies occur. Such solutions must be able to isolate individual endpoints in a network and stop any infection from spreading throughout the system.
- Conclusion
Since the start of 2017, fileless malware attacks have magnified in range and sophistication. According to the Ponemon Institute report, traditional antivirus solutions became ineffective with four out of five organizations disgruntled with their existing antivirus packages. On the other hand, Endpoint solutions are increasingly deployed as organizations turn their focus from network solutions to a multi-layered security approach. Moreover, traditional network security isn’t solely ineffective, it’s conjointly tough and expensive to manage. Despite the risks exhibit by fileless malware, steps to mitigate against the threat are comparatively simple and inexpensive. The education of home consumers and company employees is certainly one altogether the foremost effective ways in which of reducing the possibility of fileless malware infection, and campaigns that unfold the message of the danger from this type of malware ought to be increased.
References
- https://us.norton.com/internetsecurity-malware-what-is-fileless-malware..html
- https://www.carbonblack.com/definitions/what-is-fileless-malware/
- https://www.cybereason.com/blog/fileless-malware
- https://www.intelligonetworks.com/blog/fileless-malware
- https://www.techrepublic.com/article/what-is-fileless-malware-and-how-do-you-protect-against-it/
- https://www.allot.com/resources/TB_FILELESS_MALWARE_THREAT_BULLETIN.pd_.pdf
Mukul Ahmed
Incident Handler, BGD e-GOV CIRT










