Egregor Ransomware
by CIRT Team
Egregor is a ransomware from the Sekhmet malware family that has been active since the middle of September 2020. The ransomware group hacks into companies, steals information, and finally encrypts all the data.
The level of sophistication of their attacks, adaptability to infect such a broad range of victims, and significant increase in their activity suggests that Egregor ransomware operators have been developing their malware for some time and are just now putting it to (malicious) use.
Egregor is probably the most aggressive ransomware family in terms of negotiation with the victims. Its operators give only 72 hours to contact them. If the ransom is not paid, the data is released to the public via the attacker’s website, “Egregor News.”
The ransomware payment is negotiated and agreed upon via a special chat function assigned to each victim. The payment is received in bitcoin.
The information available so far suggests that the initial infection starts with a phishing email that contains a malicious macro embedded in an attached document.

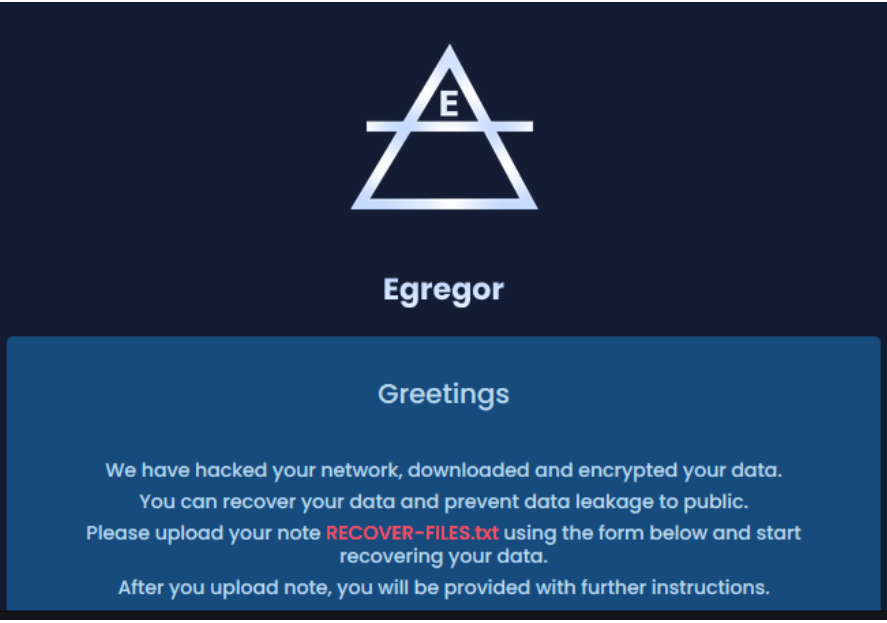
Message shown to infected users
Perform regular backups of all critical information to limit the impact of data or system loss and to help expedite the recovery process. Ideally, this data should be kept on a separate device, and backups should be stored offline.
Leverage Pretty Good Privacy in mail communications. Additionally, encrypt or protect the sensitive document stored in the internet-facing machines to avoid potential leakage
Maintain updated anti-virus software on all systems and don’t open attachments in unsolicited e-mails, even if they come from people in your contact list, and never click on a URL contained in an unsolicited e-mail.
It also suggested that security managers should disable remote desktop connections/limiting users who can log in using remote desktop and setting an account lockout policy and employ least-privileged accounts.
Known Indicators of Compromise (IoCs):
Indicator of compromise (IoC) in computer forensics is an artifact observed on a network or in an operating system that, with high confidence, indicates a computer intrusion.
91[.]199[.]212[.]52
49[.]12[.]104[.]241
45[.]153[.]242[.]129
185[.]238[.]0[.]233
Crt[.]sectigo[.]com
hxxp://49[.]12[.]104[.]241:81/78.bin
hxxp://49[.]12[.]104[.]241/sm.dll
hxxp://49[.]12[.]104[.]241:81/sm.dll
03cdec4a0a63a016d0767650cdaf1d4d24669795
069ef8443df750e9f72ebe4ed93c3e472a2396e2
072ab57f9db16d9fb92009c8e10b176bd4a2eff01c3bc6e190020cf5a0055505
07d4bcb5b969a01fb21dc28e5cb1b7ceb05f2912
16a9c2917577e732cd6630b08e248443
1a722cde21a4338b26bc37401ef963022d97cea141c985e6615a10287f8d02ff
1cce0c0d67fe7f51f335a12138698403
28f3f5a3ea270d9b896fe38b9df79a6ca430f5edab0423b3d834cf8d586f13e6
2d01c32d51e4bbb986255e402da4624a61b8ae960532fbb7bb0d3b0080cb9946
386cf4e151bc7510c3333eb1a5c96ab1b7becd8cfb94bcb76e93458078daf66f
3dba9fbef8f8a42ecfa65022b8a3c54738d15ef67c666272078b58b3c9a0a414
410afc5daebd7b39410b046286b814bb5fb5f9139167cd310bc59cc4461d4083
43445fbe21cf3512724646a284d3e5d7
49b3d9c3bd6b6a13f89f0e849d80531454cc5cd259cbb7c8a806c67cd403575e
4c36c3533a283e1aa199f80e20d264b9
5455d104e693445dce5567236f4e047617bae7f09d5ca8699a838c2d17d37fb3
561092877e91f2741ed061cbe7a57d1af552b600c6654ccc588cb6bff7939152
5f9fcbdf7ad86583eb2bbcaa5741d88a
605c2047be7c4a17823ad1fa5c1f94fd105721fce3621dc9148cd3baf352938e
627c2219a80245a25e4fe9843ac2a021
65c320bc5258d8fa86aa9ffd876291d3
7222c8acc69a7598989c335d528b366f801a41b434cbf928c6aef01f8e54f57a
7bc6c2d714e88659b26b6b8ed6681b1f91eef6af
7caed5f406445c788543f55af6d98a8bc4f0c104e6a51e2564dd37b6a485cc18
7dd1a1a0eefc5a653a30010f475cc37c
9fffabede0ef679970666f04184340437cd70bc8fe870ee8174713ececf32398
a654b3a37c27810db180822b72ad6d3e
ac634854448eb8fcd3abf49c8f37cd21f4282dde
b027467332243c8186e59f68ff7c43c9e212d9e5074fedf003febcfedad4381a
b554791b5b161c34b0a7d26e34a88e60
b81d2293b43decd5a401487da952deb32cbb53f118882b97b457a14c67029247
b9dcee839437a917dde60eff9b6014b1
bd8c52bb1f5c034f11f3048e2ed89b7b8ff39261
c1c4e677b36a2ee6ae858546e727e73cc38c95c9024c724f939178b3c03de906
c9d46c319ed01c183598f7b9a60b9bca34b2eea989f4659e9aa27c7a1bf8681c
d2d9484276a208641517a2273d96f34de1394b8e
d6fa64f36eab990669f0b81f84b9a78a
e0caae0804957c5e31c53dd320ca83a5465169c9
e27725074f7bc55014885921b7ec8b5319b1ef8f
e3ef50749f144bfd7f5d7d51aaa9e2332b706c4d8ac130fdc95f50662525f6e0
ed5b60a640a19afe8d1281bf691f40bac34eba8a
f0215aac7be36a5fedeea51d34d8f8da2e98bf1b
f1ba626b8181bd1cd84f47f70838d9fa4d8117fac3bd07cbd73cb6f73b1297f8
f7bf7cea89c6205d78fa42d735d81c1e5c183041
5a346fb957abeba389424dc57636edcacc58b5ba
901cee60fba225baf80c976b10dfa1684a73f5ee
a6259615ea10c30421e83d20f4a4b5f2c41b45b8
03cdec4a0a63a016d0767650cdaf1d4d24669795
4ea064f715c2a5f4ed68f57029befd8f406671dd
ac634854448eb8fcd3abf49c8f37cd21f4282dde
7bc6c2d714e88659b26b6b8ed6681b1f91eef6af
0579da0b8bfdfce7ca4a45baf9df7ec23989e28b
3a33de9a84bbc76161895178e3d13bcd28f7d8fe
f7bf7cea89c6205d78fa42d735d81c1e5c183041
986f69a43e0bf174f73139785ec8f969acf5aa55
f1603f1ddf52391b16ee9e73e68f5dd405ab06b0
5a346fb957abeba389424dc57636edcacc58b5ba
901cee60fba225baf80c976b10dfa1684a73f5ee
a6259615ea10c30421e83d20f4a4b5f2c41b45b8
4ea064f715c2a5f4ed68f57029befd8f406671dd
f73e31d11f462f522a883c8f8f06d44f8d3e2f01
ac6d919b313bbb18624d26745121fca3e4ae0fd3
95aea6b24ed28c6ad13ec8d7a6f62652b039765e
a786f383dfb90191aa2ca86ade68ee3e7c088f82
631924a3567390a081dbd82072a6fc3a185c5073
1be22505a25f14fff1e116fafcaae9452be325b1
a2d5700def24c3ae4d41c679e83d93513259ae4a
34a466a0e55a930d8d7ecd1d6e6c9c750082a5fe
2edaa3dd846b7b73f18fa638f3e1bc3a956affa4
Reference:
- https://www.digitalshadows.com/blog-and-research/egregor-the-new-ransomware-variant-to-watch/
- https://www.cybereason.com/blog/cybereason-vs-egregor-ransomware
- https://www.bankinfosecurity.com/egregor-ransomware-adds-to-data-leak-trend-a-15110










