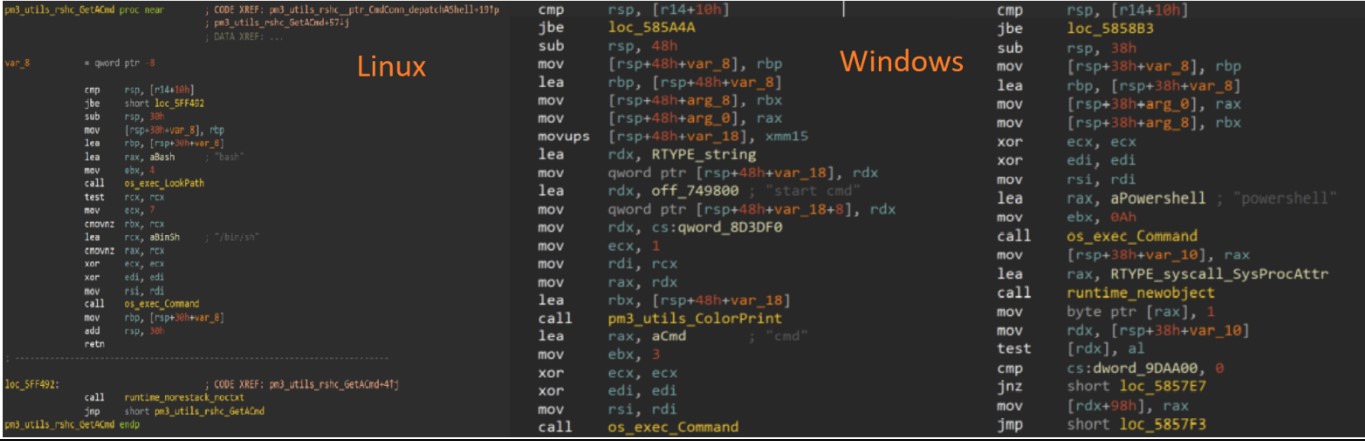
A new Ducktail phishing campaign is spreading a never-before-seen Windows information-stealing malware written in PHP used to steal Facebook accounts, browser data, and cryptocurrency wallets. Ducktail phishing campaigns were first revealed by researchers from WithSecure in July 2022, who linked the attacks to Vietnamese hackers. Those campaigns relied on social engineering attacks through LinkedIn, pushing .NET Core malware masquerading as a PDF document supposedly containing details about a marketing...
Read More
A recent malicious campaign delivering Magniber ransomware has been targeting Windows home users with fake security updates. Threat actors created in September websites that promoted fake antivirus and security updates for Windows 10. The downloaded malicious files (ZIP archives) contained JavaScript that initiated an intricate infection with the file-encrypting malware. A report from HP’s threat intelligence team notes that Magniber ransomware operators demanded payment of up to $2,500...
Read More
Experts discovered a new attack framework, including a C2 tool dubbed Alchimist, used in attacks against Windows, macOS, and Linux systems. Researchers from Cisco Talos discovered a new, previously undocumented attack framework that included a C2 dubbed Alchimist. The framework is likely being used in attacks aimed at Windows, macOS, and Linux systems. The experts also spotted a new GoLang malware dubbed Insekt supporting remote...
Read More
Vulnerability DescriptionAn issue was discovered in Zimbra Collaboration (ZCS) 8.8.15 and 9.0. An attacker can upload arbitrary files through amavisd via a cpio loophole (extraction to /opt/zimbra/jetty/webapps/zimbra/public) that can lead to incorrect access to any other user accounts. Zimbra recommends pax over cpio. Also, pax is in the prerequisites of Zimbra on Ubuntu; however, pax is no longer part of a default Red Hat installation...
Read More
licious cyber actors continue to exploit known vulnerabilities and use publicly available tools to target networks of interest. Remote code execution (RCE) attacks allow an attacker to remotely execute malicious code on a computer. The impact of an RCE vulnerability can range from malware execution to an attacker gaining full control over a compromised machine. RCE vulnerabilities are some of the most risky and high-impact...
Read More
Signal says it will start to phase out SMS and MMS message support from its Android app to streamline the user experience and prioritize security and privacy. While this announcement may surprise those who don’t know Signal can also be used to manage this type of text message, the Signal for Android app could be configured as the default SMS/MMS app since its beginning as TextSecure, an...
Read More
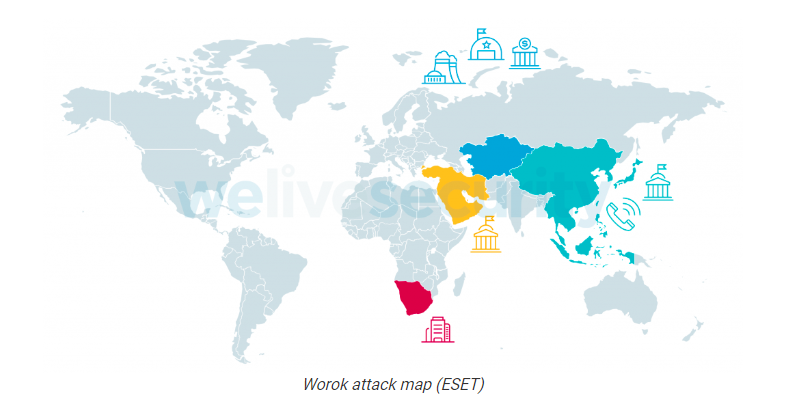
A new cyber espionage threat group that has been previously unknown named Worok and has been observed using undocumented tools targeting private and local government entities mostly in Asia. Based on the report by ESET, the group has been active for at least 2020 and observed a significant break in operation from 2021-05 to 2022-01, but in 2022-02, their operation resumed, targeting an energy company, and a public...
Read More
An authentication bypass using an alternate path or channel vulnerability [CWE-288] in FortiOS, FortiProxy and FortiSwitchManager may allow an unauthenticated atttacker to perform operations on the administrative interface via specially crafted HTTP or HTTPS requests. Exploitation Status: Fortinet recommends immediately validating systems against the following indicator of compromise in the device’s logs:user=”Local_Process_Access” Affected ProductsFortiOS version 7.2.0 through 7.2.1FortiOS version 7.0.0 through 7.0.6FortiProxy version 7.2.0FortiProxy version...
Read More
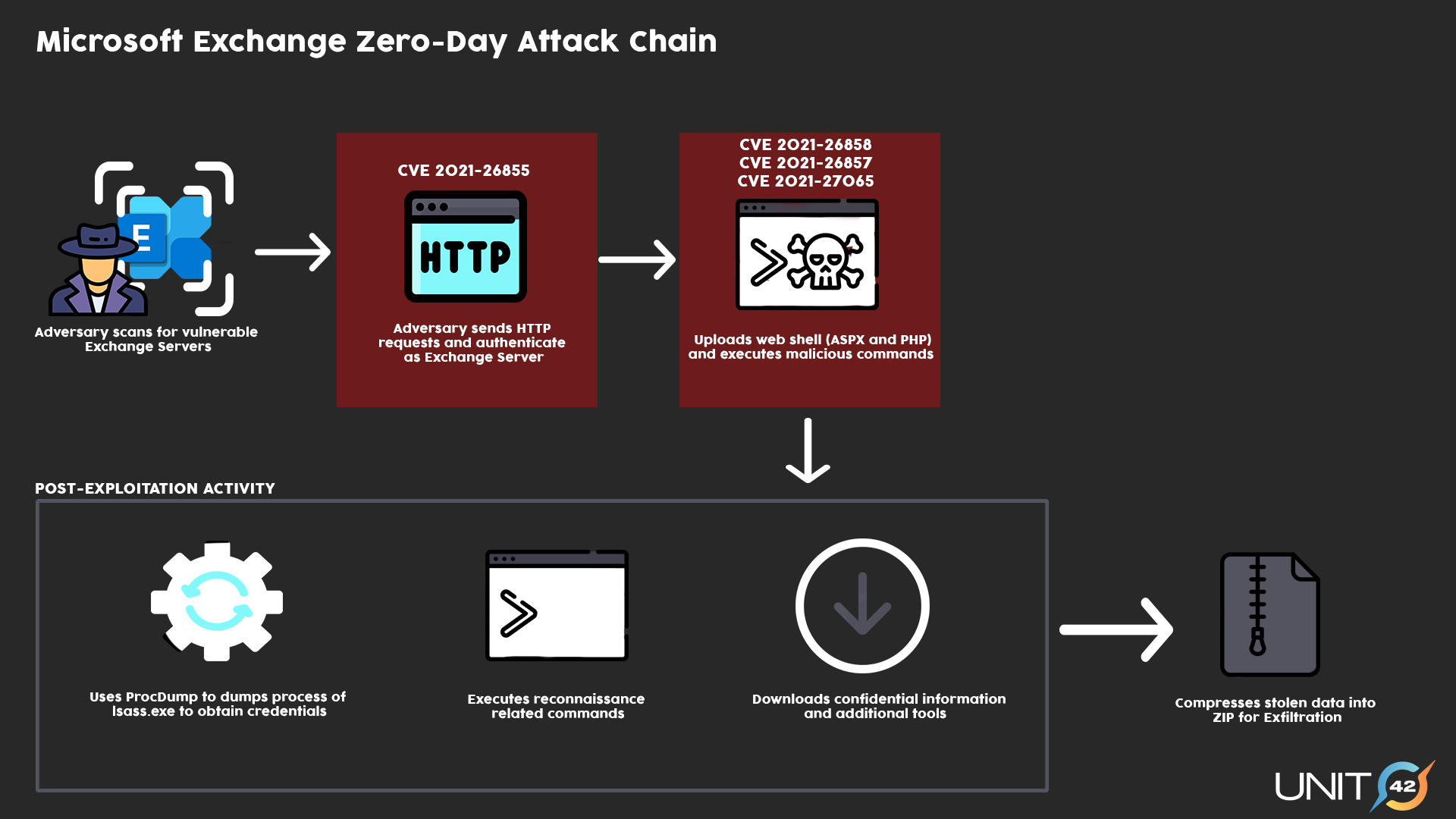
Microsoft has confirmed that two reported zero-day vulnerabilities in Microsoft Exchange Server 2013, 2016, and 2019. The first one, identified as CVE-2022-41040, is a Server-Side Request Forgery (SSRF) vulnerability, and the second one, identified as CVE-2022-41082, allows Remote Code Execution (RCE) when PowerShell is accessible to the attacker. From the note Microsoft added, CVE-2022-41040 can enable an authenticated attacker to remotely trigger CVE-2022-41082. It should...
Read More
Hackers backed by the North Korean government are weaponizing well-known pieces of open source software in an ongoing campaign that has already succeeded in compromising “numerous” organizations in the media, defense and aerospace, and IT services industries, Microsoft said on Thursday. ZINC—Microsoft’s name for a threat actor group also called Lazarus, which is best known for conducting the devastating 2014 compromise of Sony Pictures Entertainment—has been...
Read More