Operation Soft Cell: A Worldwide Campaign Against Telecommunications Providers
by CIRT Team
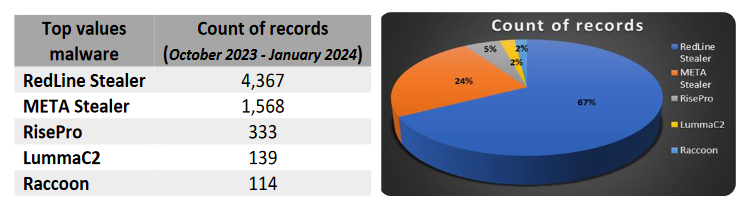
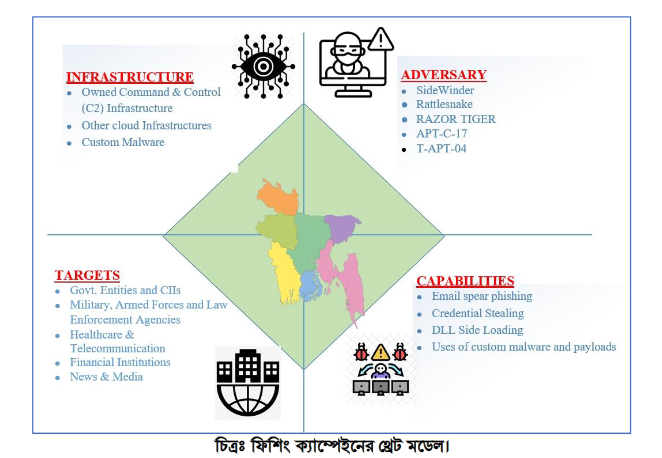
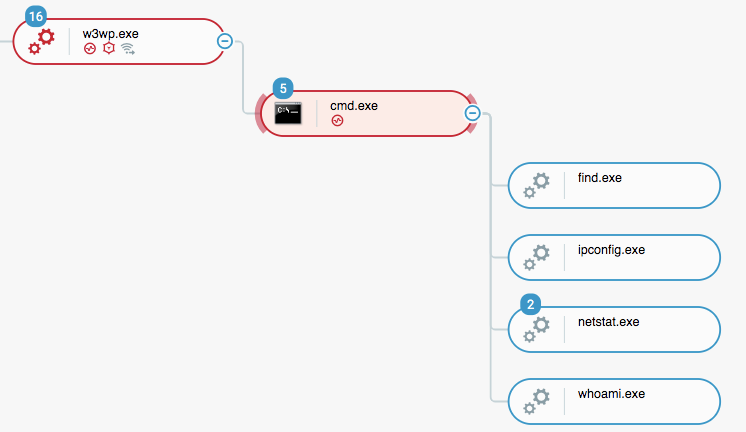
An advanced, persistent attack targeting telecommunication providers, active since at least 2012, according to Cybereason researchers. The attack, dubbed Operation Soft Cell, was aiming to obtain all data stored in the active directory of a large telecommunications provider, compromising usernames and passwords within the organization, as well as billing information, call detail records, credentials, email servers, and personal identifiable information. The attack consisted of customized and highly-modified versions of the China Chopper web shell, Poison Ivy rat, and “mimikatz” to ultimately obtain credentials. The attackers worked in waves, abandoning one thread of the attack when detected and stopped, but would return months later with new techniques. Cybereason believes with a high level of certainty that the threat actor is affiliated with China and is likely state-sponsored. The tools and techniques used throughout these attacks are consistent with several Chinese actors believed to operate on behalf of the Chinese Ministry of State Security.

Recommendation: Defense-in-depth (layering of security mechanisms, redundancy, fail-safe defense processes) is the best way to ensure safety from APTs, including a focus on both network and host-based security. Prevention and detection capabilities should also be in place.
Reference: https://securelist.com/mobile-banker-riltok/91374/
Recommended Posts
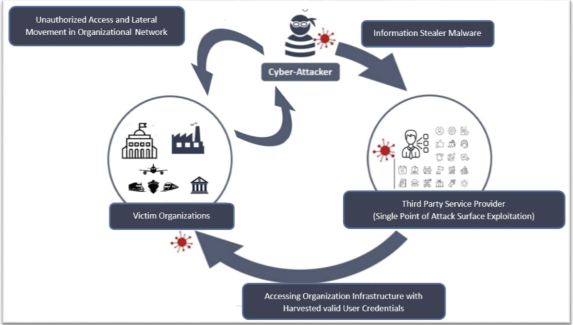
Cyber Threat Alert: Surge in Attacks via Compromised Third-Party Service Providers
08 Feb 2024 - Articles, English articles, Security Advisories & Alerts