CVE-2020-12695 : Data Exfiltration & Reflected Amplified TCP DDOS & Port Scan
by CIRT Team
The Open Connectivity Foundation UPnP specification before 2020-04-17 does not forbid the acceptance of a subscription request with a delivery URL on a different network segment than the fully qualified event-subscription URL, aka the CallStranger issue.
What is UPnP?
Universal Plug and Play (UPnP) is a set of networking protocols that permits networked devices, such as personal computers, printers, Internet gateways, Wi-Fi access points and mobile devices to seamlessly discover each other’s presence on the network and establish functional network services for data sharing, communications, and entertainment. UPnP is intended primarily for residential networks without enterprise-class devices.
The vulnerability:
The vulnerability – CallStranger – is caused by Callback header value in UPnP SUBSCRIBE function can be
changed by an attacker and causes a kind of SSRF vulnerability on millions of devices.
Because this is a protocol vulnerability, it may take long time for vendors to provide patches.
Impact:
An attacker can use this vulnerability for
• Bypassing DLP for exfiltrating data
• Using millions of Internet-facing UPnP device as source of amplified reflected TCP DDoS (not same
with https://www.cloudflare.com/learning/ddos/ssdp-ddos-attack/ )
• Scanning internal ports from Internet facing UPnP devices
Enterprises should
• Disable unnecessary UPnP services especially for Internet facing devices/interfaces.
• Check Intranet and server networks to be sure UPnP devices (Routers, IP cameras, printers,
media gateways etc.) is not allowing data exfiltration.
• Make assessment on network security logs if this vulnerability had been used any threat actor.
• Contact to ISP/ DDoS protection vendor if their solutions can block traffic generated by UPnP
SUBSCRIBE (HTTP NOTIFY)
Technical Mitigations
It may take long time for vendors to patch UPnP devices, enterprises should take their own actions.
Depending on defense-in-dept approach, enterprises may choose different mitigations.
A. Internet facing devices
1. Close UPnP Ports to Internet if there is no business/technical requirement.
2. Close UPnP Services’ port (different from UDP 1900) to Internet. To find out these ports check
products documentation or use a port scanner or UPnP Device Spy.
B. Security Devices
1. Block all SUBSCRIBE and NOTIFY HTTP packets in ingress and egress traffic.
2. Check logs if anyone used this vulnerability
3. Configure DDoS protection device or service to block NOTIFY packets
C. Intranet
1. Disable UPnP service of IP camera, printer, routers and other devices if it is not a business or
technical requirement.
2. Check these devices’ Internet access policy (B1)
D. DMZ & Server Segment
1. Don’t place unsecured UPnP devices on this network
2. Be careful for media processing servers. Media services may use UPnP. Do (B1) if it doesn’t affect
business and technical requirements.
Apply updates
Vendors are urged to implement the updated specification provided by the OCF.
Users should monitor vendor support channels for updates that implement the new SUBSCRIBE specification.
Reference:
https://callstranger.com
https://kb.cert.org/vuls/id/339275
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-12695
https://www.tenable.com/blog/cve-2020-12695-callstranger-vulnerability-in-universal-plug-and-play-upnp-puts-billions-of
Recommended Posts
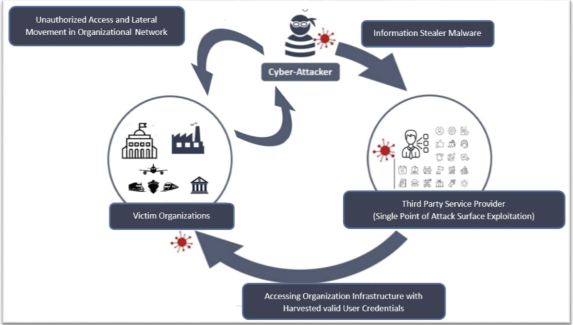
Cyber Threat Alert: Surge in Attacks via Compromised Third-Party Service Providers
08 Feb 2024 - Articles, English articles, Security Advisories & Alerts