A Vulnerability in Confluence Server and Data Center Could Allow for Arbitrary Code Execution
by CIRT Team
DESCRIPTION:
A vulnerability has been discovered in Confluence Server and Data
Center, which could allow for arbitrary code execution. Confluence is a
wiki tool used to help teams collaborate and share knowledge
efficiently. Successful exploitation of this vulnerability could allow
an unauthenticated user to execute arbitrary code on a Confluence Server
or Data Center instance. Depending on the privileges associated with the
instance, an attacker could view, change, or delete data.
IMPACT:
US Cyber Command has reported mass exploitation of CVE-2021-26084 and
anticipates accelerated attack volume.
SYSTEM AFFECTED:
* Confluence Server and Data Center all versions prior to 6.13.23
* Confluence Server and Data Center versions from 6.14.0 prior to 7.4.11
* Confluence Server and Data Center versions from 7.5.0 prior to 7.11.6
* Confluence Server and Data Center versions 7.12.x prior to 7.12.5
RECOMMENDATIONS:
We recommend the following actions be taken:
* Apply appropriate patches provided by Atlassian to vulnerable systems
immediately after appropriate testing.
* Run all software as a nonprivileged user (one without administrative
privileges) to diminish the effects of a successful attack.
* Evaluate read, write, and execute permissions on all newly installed
software.
* Apply the Principle of Least Privilege to all systems and services.
REFERENCES:
https://confluence.atlassian.com/doc/confluence-security-advisory-2021-08-25-1077906215.html
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-26084
Recommended Posts
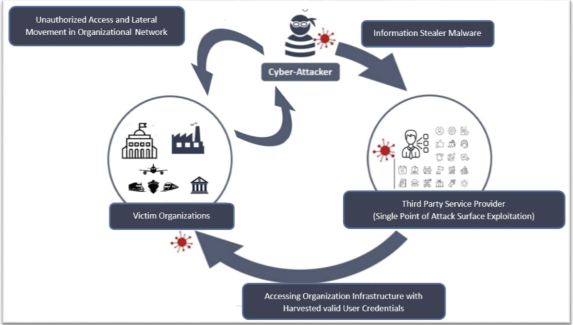
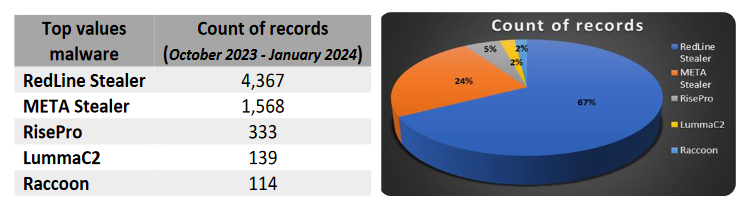
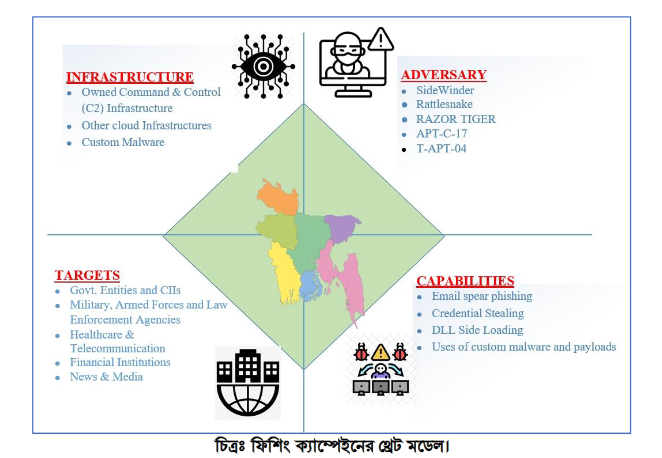
Cyber Threat Alert: Surge in Attacks via Compromised Third-Party Service Providers
08 Feb 2024 - Articles, English articles, Security Advisories & Alerts