Emerging Phishing Attack on Cyber Space of Bangladesh

by CIRT Team
TLP: CLEAR
Distribution: Public
Type of Threat: Phishing E-Mail
Date: 12 January 2025
Executive Summary
Recently, we have observed a surge in phishing attacks targeting various government organizations, law enforcement agencies, educational institutions, and others, with the attacks spreading further through compromised accounts. This campaign is targeted to steal sensitive information by impersonating official entities and leveraging malicious attachments and links. This advisory provides details on phishing email contents, Indicators of Compromise (IOCs), and detection rules to raise awareness and enhance security.
Most Targeted Sectors
- Government Organizations
- Law Enforcement Agencies
- Educational Institutions
Breakdown of Phishing Email Contents
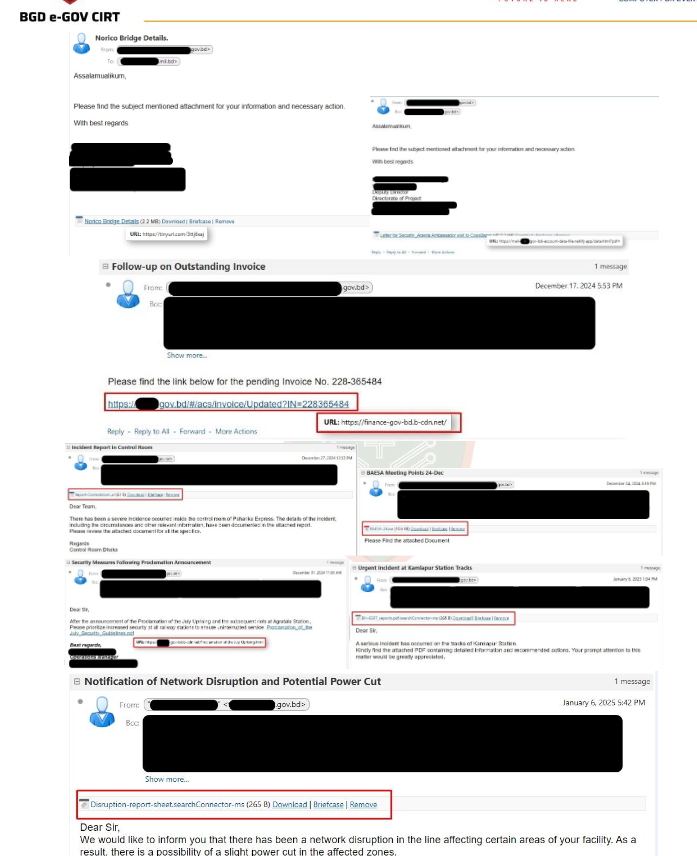
- Subject and Sender:
- Subject lines mimic official communication such as security notifications or updates.
- Sender addresses are spoofed to appear legitimate, often resembling government or organizational email domains.
- Body Content:
- Formal greetings and language to establish authenticity.
- Request for urgent action, such as clicking links or downloading attachments.
- References to official-sounding documents or procedures.
- Attachments:
- Files with extensions like .rar, .pdf, .url, .html, and renamed files like -ms to bypass filters.
- Phishing Links:
- Redirect to fake login pages or forms that collect sensitive information.
Phishing Email Analysis
Main Suspicious Link
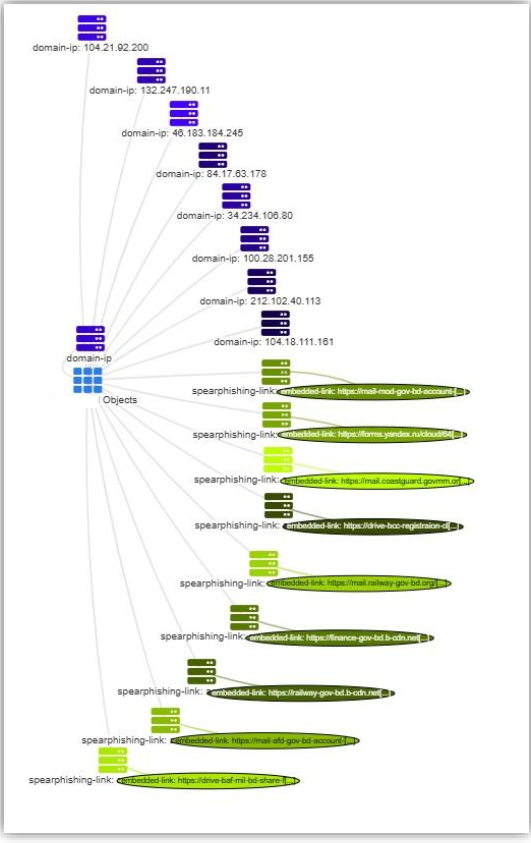
https[:] / / mail-mod-gov-bd-account-data-file[.]netlify.app/data[.]html?pdf=
Domain: mail-mod-gov-bd-account-data-file[.]netlify[.]app
- This is a subdomain of netlify.app, commonly used for hosting free websites.
- The domain mimics a government-related name (gov-bd) to appear legitimate.
Path: /data[.] html
The generic filename (data.html) does not align with the official communication of sensitive documents.
Query Parameter: [?] pdf=
No actual PDF is linked, further raising suspicion.
Alternate Download Link
https[:] / / mail[.]coastguard.govmm[.]org/ULfwhxNc
Another suspicious link targeting users with a government-like domain to appear legitimate.
Generic Placeholder Links
https[:]// briefcase
https[:]// remove
These links are non-functional and are likely placeholders. The use of these links indicates a lack of legitimacy as no reputable sender would include such incomplete URLs.
Indicators of Phishing
Domain Spoofing: The domain name mail -mod-gov-bd-account-data-file is designed to mimic official government domains but is hosted under netlify.app, a free hosting service.
Non-functional Links: Placeholder links (https[:]// briefcase, https[:]// remove) highlight a lack of legitimacy.
Attachment Mismatch: The email mentions an attachment (e.g., Letter for Security Algeria Ambassador visit to CoxsBazar.pdf), but the link leads to a suspicious page instead of an actual file.
Content Encoding: The email content is encoded (e.g., quoted-printable), making it harder to analyze at a glance.
Examples of Phishing Emails
Indicators of Compromise (IOCs):
| IP Addresses | 34.234.106[.]80 |
| 104.21.92[.]200 | |
| 84.17.63[.]178 | |
| 212.102.40[.]113 | |
| 100.28.201[.]155 | |
| 132.247.190[.]11 | |
| 104.18.111[.]161 | |
| 46.183.184[.]245 | |
| Attached File Extension | .rar |
| .url | |
| .html | |
| -ms (file renamed as -ms to bypass filters) | |
| Phishing Links | https[:]//drive-baf-mil-bd-share-file.netlify.app/airforce%20drive%20share |
| https[:]//drive-bcc-registraion-cloud-storage.netlify.app/bcc%20drive%20share | |
| https[:]//railway-gov-bd.b-cdn.net/Proclamation%20of%20the%20July%20Uprising.html | |
| https[:]//railway-gov-bd.b-cdn.net/Proclamation%20of%20the%20July%20Uprising.html | |
| https[:]//mail-mod-gov-bd-account-data-file.netlify.app/data.html?pdf= | |
| https[:]//forms.yandex.ru/cloud/64d311e643f74f24f282c9e6 | |
| https[:]// mail-afd-gov-bd-account-error-issues.netlify.app/afd.html?afd=admin_dte@afd[.]gov.bd | |
| https[:]//mail.railway-gov-bd.org | |
| https[:]//mail.coastguard.govmm.org/ULfwhxNc |
MITRE ATT&CK Mapping:
Tactic: Initial Access (TA0001)
Overview of Phishing Campaign Infrastructure IP addresses and links:
Technical Detection Rules: (BGD e-GOV CIRT)
Note:
The following rules are provided as samples to assist technical teams in utilizing Indicators of Compromise (IoCs) for threat hunting or threat detection purposes. These rules may need to be customized to align with the specific fields and configurations of your SIEM and other security monitoring tools. Always review and adapt these rules to fit your operational environment and security requirements.
Suricata Rules
alert http any any -> any any (msg:”Phishing URL detected – mail-mod-gov-bd”; content:”mail-mod-gov-bd-account-data-file”; http_host; classtype:trojan-activity; sid:1000001; rev:2;)
alert http any any -> any any (msg:”Phishing URL detected – Coast Guard”; content:”mail.coastguard.govmm.org”; http_host; classtype:trojan-activity; sid:1000002; rev:2;)
alert ip any any -> any any (msg:”Phishing IP detected – 46.183.184.245″; ip_dst:46.183.184.245; classtype:trojan-activity; sid:1000003; rev:2;)
alert ip any any -> any any (msg:”Phishing IP detected – 34.234.106.80″; ip_dst:34.234.106.80; classtype:trojan-activity; sid:1000004; rev:2;)
Sigma Rules
- Sigma Rule 1: Suspicious IP Address Connection
| title: Suspicious IP Address Connection
description: Detects connections to known malicious IP addresses. author: CTI unit of BGD e-GOV CIRT logsource: category: network product: network detection: selection: # Replace ‘network.src_ip’ and ‘network.dest_ip’ with the appropriate fields for your platform # Example field mappings: # – Splunk: src_ip, dest_ip # – Elastic ECS: source.ip, destination.ip # – Wazuh: data.srcip, data.dstip network.src_ip|endswith: – ‘34.234.106.80’ – ‘104.21.92.200’ – ‘84.17.63.178’ – ‘212.102.40.113’ – ‘100.28.201.155’ – ‘132.247.190.11’ – ‘104.18.111.161’ – ‘46.183.184.245’ network.dest_ip|endswith: – ‘34.234.106.80’ – ‘104.21.92.200’ – ‘84.17.63.178’ – ‘212.102.40.113’ – ‘100.28.201.155’ – ‘132.247.190.11’ – ‘104.18.111.161’ – ‘46.183.184.245’ condition: selection fields: – src_ip – dest_ip # Guidelines for Adapting This Rule: # 1. Understand your platform’s field names: # – Splunk: src_ip, dest_ip # – Elastic ECS: source.ip, destination.ip # – Wazuh: data.srcip, data.dstip # 2. Identify relevant fields in your logs by inspecting sample events. # 3. Replace the field names in ‘detection’ with your platform-specific field names. # 4. Use tools like Uncoder.io for automated translations and manual adjustments as needed. # 5. Test the translated query on your platform to validate results. |
- Sigma Rule 2: Phishing Link Detected
| title: Phishing Link Detected
description: Detects access to known phishing links. author: CTI unit of BGD e-GOV CIRT logsource: category: network product: network detection: selection: # Replace ‘network.http_uri’ with the appropriate fields for your platform # Example field mappings: # – Splunk: uri # – Elastic ECS: url.path # – Wazuh: http.url network.http_uri|endswith: – ‘drive-baf-mil-bd-share-file.netlify.app’ – ‘drive-bcc-registraion-cloud-storage.netlify.app’ – ‘railway-gov-bd.b-cdn.net’ – ‘finance-gov-bd.b-cdn.net’ – ‘mail-mod-gov-bd-account-data-file.netlify.app’ – ‘forms.yandex.ru’ – ‘mail-afd-gov-bd-account-error-issues.netlify.app’ – ‘mail.railway-gov-bd.org’ – ‘mail.coastguard.govmm.org’ network.http_uri|contains: – ‘drive-baf-mil-bd-share-file.netlify.app’ – ‘drive-bcc-registraion-cloud-storage.netlify.app’ – ‘railway-gov-bd.b-cdn.net’ – ‘finance-gov-bd.b-cdn.net’ – ‘mail-mod-gov-bd-account-data-file.netlify.app’ – ‘forms.yandex.ru’ – ‘mail-afd-gov-bd-account-error-issues.netlify.app’ – ‘mail.railway-gov-bd.org’ – ‘mail.coastguard.govmm.org’ condition: selection fields: – http_uri # Guidelines for Adapting This Rule: # 1. Understand your platform’s field names: # – Splunk: uri # – Elastic ECS: url.path # – Wazuh: http.url # 2. Identify relevant fields in your logs by inspecting sample events. # 3. Replace the field names in ‘detection’ with your platform-specific field names. # 4. Use tools like Uncoder.io for automated translations and manual adjustments as needed. # 5. Test the translated query on your platform to validate results. |
Actions Required:
To mitigate the risk, the following measures are recommending:
- Be Alert:
- Avoid clicking on unknown links or downloading suspicious attachments.
- Verify sender email addresses carefully to detect impersonation.
- Report Suspicious Emails:
- Forward phishing emails to the IT/security team or use “Report Phishing” tools.
- Protect Credentials:
- Never share login details via email or on unofficial websites.
- Enable multi-factor authentication (MFA) for all critical accounts.
- Training and Awareness:
- Participate in phishing awareness sessions and simulated tests.
- Stay updated on common phishing tactics and red flags.
- IOC Monitoring:
- Use the provided Indicators of Compromise (IOCs) list, Suricata Rule (for Network Traffic) and Sigma Rules (for SIEM Query) to create threat hunt and detection rules.
- Continuously monitor systems and logs for suspicious activity.
- System Security:
- Patch and update all systems and software to prevent vulnerabilities.
- Apply the principle of least privilege to user accounts and audit permissions regularly.
- Use email filtering and sandboxing to block malicious attachments or links.
- Incident Response:
- Ensure an active and tested incident response plan is in place.
- Act promptly on reported phishing incidents to contain threats.
- Report or inform BGD e-GOV CIRT, BCC regarding any IOC’s or suspicious activities within your infrastructure, through mail id: cirt@cirt.gov.bd or cti@cirt.gov.bd
You can find the full PDF Document here