ABOUT “BLUEBLEED”SERVICE AND THE VULNERABILITY OF MICROSOFT AWS SERVERS

Attack info
First seen 2022-09-24 • Last seen 2022-10-19
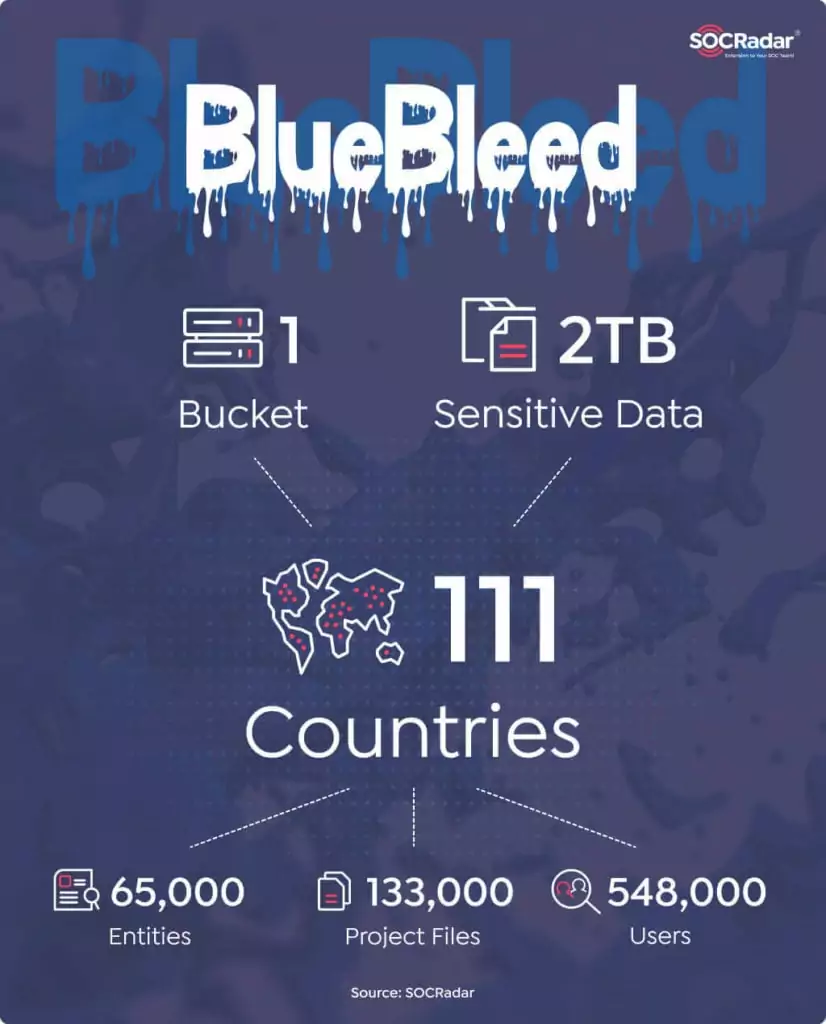
On October 19, 2022, Socradar announced a vulnerability they discovered in several misconfigured
Microsoft AWS servers. They also announced the launch of the BlueBleed service, which contains data
downloaded from several misconfigured Microsoft AWS servers.
Link to the Socradar announcement – hxxps://socradar[.]io/sensitive-data-of-65000-entities-in-111-
countries-leaked-due-to-a-single-misconfigured-data-bucket/
The exposed files in the misconfigured bucket include;
POE documents,
SOW documents,
Invoices,
Product orders,
Product offers,
Project details,
Signed customer documents,
POC (Proof of Concept) works,
Customer emails (as well as .EML files),
Customer product price list and customer stocks,
Internal comments for customers (High risk etc.),
Sales strategies,
Customer asset documents, and
Partner ecosystem details.
How to Prevent Data Leaks due to Misconfigured Servers?
Misconfigured servers are one of the top reasons for data leaks. According to the SANS 2022 Top New Attacks and Threat Report, cloud storage data exfiltration has become one of the most common attack paths in 2022.
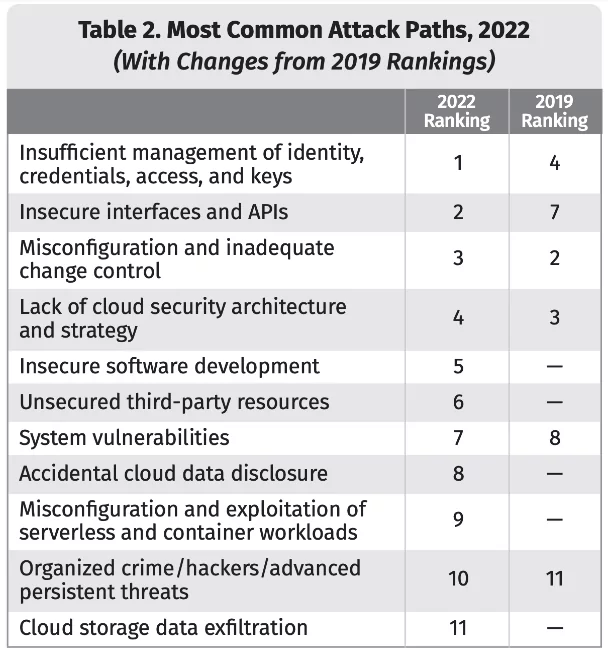
Threat actors constantly scan public storage buckets for sensitive data. They have the resources and means to automate the scanning with advanced tools. Companies should proactively monitor such cyber risks with automated security tools.
- Map out your attack surface to easily manage and control external-facing endpoints.
- Apply your shared responsibility model
- Bring identity and access solutions to all your environments
- A shared access signature token should be used for providing controlled and timed access to your blob containers.
- Encrypt your data at rest
- Enforce accepted cloud security policies – Zero Trust approach
- Fortify your endpoints to prevent breaches.
- Monitor your attack surface to detect any external assets open to the public, which may contain sensitive data about your company and your customers.
This case is not a typical data breach. Socradar found several misconfigured Microsoft AWS servers.
It’s not a rare case, usually, all researchers, who found such servers, just notify the owner of it
to fix the issue. But Socradar uploaded this data to themselves, which is not a completely legal
action, in connection with this, our Сompany does not engage in such research and never copies
third-party data to itself if it has not been published in the public.
Socradar notified Microsoft about the find on September 24, 2022, after which the entire
vulnerability was fixed and the data is no longer available. There is no such leak anywhere in the
public, there is no evidence that the Threat Actors managed to find these servers and download the
data before Socradar. We will be monitoring the underground for this leak and will notify our
Customers as soon as we find it.
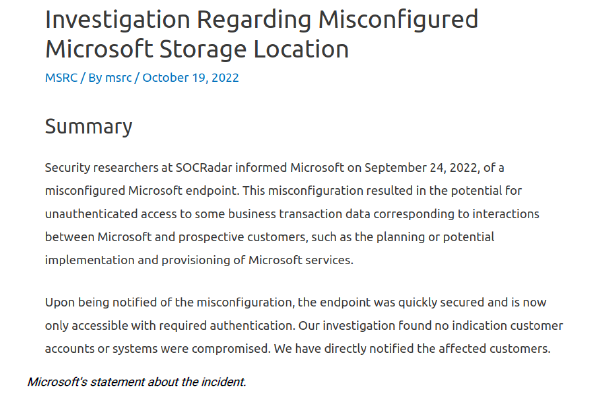
Microsoft released a statement regarding the incident.
You can read it at the following link –
https://msrc-blog.microsoft.com/2022/10/19/investigation-regarding-
misconfigured-microsoft-storage-location-2/.
Microsoft claims that representatives of Socradar greatly exaggerate the extent of the leak
(Microsoft’s own investigation showed that there are many duplicates and redirects among the
affected data). Microsoft is also concerned and disappointed by the fact that Socradar not only
informed Microsoft about the problem but also took advantage of this data, making it available in
its service, which is contrary to the basic principles of ensuring data protection and
confidentiality of user data. Microsoft also stated that directly notified the affected customers.
Check if you are exposed: https://socradar.io/labs/bluebleed