Multiple Vulnerabilities in Apple Products Could Allow for Arbitrary Code Execution
by CIRT Team
DESCRIPTION:
Multiple vulnerabilities have been discovered in Apple Products, the
most severe of which could allow for arbitrary code execution.
* tvOS is an operating system for the fourth-generation Apple TV digital
media player.
* watchOS is the mobile operating system for the Apple Watch and is
based on the iOS operating system.
* iPadOS is the successor to iOS 12 and is a mobile operating system for
iPads.
* iOS is a mobile operating system for mobile devices, including the
iPhone, iPad, and iPod touch.
* Xcode is an integrated development environment (IDE) for macOS.
Successful exploitation of the most severe of these vulnerabilities
could result in arbitrary code execution within the context of the
application, an attacker gaining the same privileges as the logged-on
user, or the bypassing of security restrictions. Depending on the
permission associated with the application running the exploit, an
attacker could then install programs; view, change, or delete data.
Several of the previous vulnerabilities have been found in macOS, an
operating system for Apple desktops and laptops. Additional new
vulnerabilities have also been discovered, the most severe of which
could allow for arbitrary code execution with system privileges. An
attacker could then install programs; view, change, or delete any data.
IMPACT:
There are reports of the following vulnerabilities currently being
actively exploited in the wild:
* CVE-2021-1782: iOS, iPadOS, tvOS, watchOS vulnerability that enables
privilege escalation.
* CVE-2021-1870: WebKit vulnerability that enables arbitrary code execution.
* CVE-2021-1800: Xcode vulnerability that enables arbitrary file access.
* CVE-2021-1782: macOS vulnerability that enables privilege escalation.
* CVE-2021-1870 and CVE-2021-1871: macOS vulnerability that enables
arbitrary code execution.
SYSTEM AFFECTED:
* iOS versions prior to iOS 14.4
* iPadOS versions prior to iPadOS 14.4
* tvOS versions prior to tvOS 14.4
* watchOS versions prior to watchOS 7.3
* Xcode versions prior to Xcode 12.4
RECOMMENDATIONS:
We recommend the following actions be taken:
* Apply appropriate patches provided by Apple to vulnerable systems
immediately after appropriate testing.
* Run all software as a nonprivileged user (one without administrative
privileges) to diminish the effects of a successful attack.
* Remind users not to download, accept or execute files from untrusted
and unknown sources.
* Remind users not to visit untrusted websites or follow links provided
by untrusted or unknown sources.
* Evaluate read, write, and execute permissions on all newly installed
software.
* Apply the Principle of Least Privilege to all systems and services.
REFERENCES:
https://support.apple.com/en-us/HT212146
https://support.apple.com/en-us/HT212149
https://support.apple.com/en-us/HT212148
https://support.apple.com/en-us/HT212153
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-1782
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-1800
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-1870
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-1871
https://support.apple.com/en-us/HT212147
Recommended Posts
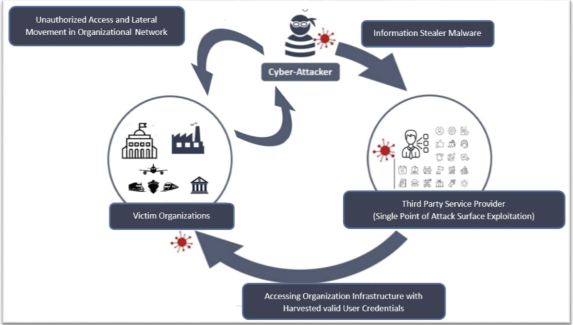
Cyber Threat Alert: Surge in Attacks via Compromised Third-Party Service Providers
08 Feb 2024 - Articles, English articles, Security Advisories & Alerts