in Security Advisories & Alerts
Vanilla Forums < 2.3 - Remote Code Execution Vulnerability
Description: Vanilla Forums software (including the latest stable version of 2.3 in its default configuration) is affected by * Host Header Injection CVE-2016-10073 which can be exploited by unauthenticated remote attackers to potentially intercept password reset hash and gain unauthorized access to the victim account or perform web-cache poisoning attacks. Impact: With victim user interaction, attacker could potentially intercept the password reset hash. This vulnerability...
Read More
in Security Advisories & Alerts
LibreOffice CVE-2017-8358: heap-based buffer overflow related to the ReadJPEG function.
Description: LibreOffice before 2017-03-17 has an out-of-bounds write caused by a heap-based buffer overflow related to the ReadJPEG function in vcl/source/filter/jpeg/jpegc.cxx. Impact: As an impact it is known to affect confidentiality, integrity, and availability. Mitigation: Updates are available. Please see the references for more information. Reference URL’s: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-8358 https://www.libreoffice.org/about-us/security/advisories/ https://security-tracker.debian.org/tracker/CVE-2017-8358 https://access.redhat.com/security/cve/cve-2017-8358 https://bugzilla.redhat.com/show_bug.cgi?id=1447279 https://www.suse.com/security/cve/CVE-2017-8358/
in Security Advisories & Alerts
SQL Injection Vulnerability in Joomla! 3.7
Description: SQL injection vulnerability in Joomla! 3.7.x before 3.7.1 allows attackers to execute arbitrary SQL commands via unspecified vectors. The vulnerability is caused by a new component, com_fields, which was introduced in version 3.7. Impact: An SQL injection flaw that allows attackers to execute custom SQL code on affected systems and take over vulnerable sites. Mitigation: Upgrade to version 3.7.1. Please check specific vendor advisory...
Read More
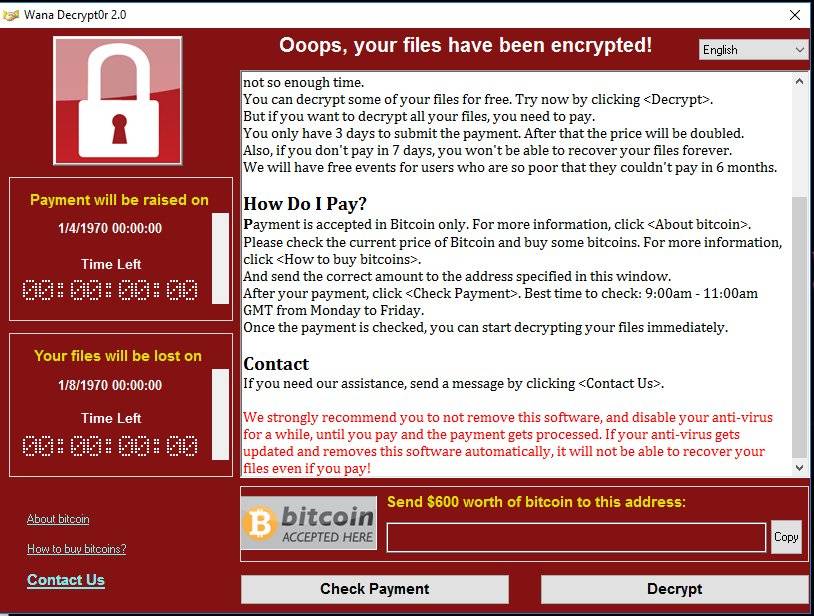
in News Clipping
What you need to know about the WannaCry Ransomware [symantec]
Can I recover the encrypted files or should I pay the ransom? Decryption of encrypted files is not possible at present. If you have backup copies of affected files, you may be able to restore them. Symantec does not recommend paying the ransom. In some cases, files may be recovered without backups. Files saved on the Desktop, My Documents, or on a removable drive are...
Read More
in Articles, English articles, News
WannaCry Malware Attack and Recommended Actions from Microsoft
Microsoft has provided guidance regarding malware variously named WannaCrypt, WannaCry, WannaCryptor, or Wcry. On May 12, 2017, many of their customers around the world and the critical systems they depend on were victims of malicious “WannaCrypt” software. Below they have given further details of the threat and steps every individual and business should take to stay protected. Additionally, Microsoft is taking the highly unusual step...
Read More