1st International Cyber Security Conference Bangladesh, 2017 has been successfully completed

by CIRT Team

The CIRT team of Bangladesh Computer Council is increasingly creating awareness of the need to seriously address the daunting challenges of protecting their information networks, especially those related to national security and critical infrastructures, from any attacker. Recent developments have shown that there is more to this endeavor than answering technical questions, particularly since many technical problems do not necessarily seem to have solutions. The cyber-security question needs to be placed within a larger framework of international cooperation, norms, and rules for appropriate and responsible state behavior that will ensure the peaceful use of cyberspace.
On this regard, the government in collaboration with cyber security and tech giants has successfully organized an international cyber security conference in the capital on 9 March 2017 aims at taking a coordinated initiative to prevent and check the alarming rise of cyber-attacks. This event was on the occasion of first anniversary of BGD e-GOV CIRT.
Leveraging ICT for Growth, Employment and Governance (LICT) of ICT Division, US based Fire Eye, CISCO, CA Technologies, Microsoft, One World InfoTech, Europe based NRD AS and Bangladesh Based companies NRD Bangladesh Ltd. & REVE Systems has jointly organized the conference at auditorium of Bangladesh Computer Council (BCC).
Mr. Zunaed Ahmed Palak, MP, Honorable Minister of ICT welcomed the participants and thanked them for their attendance. The conference opened with speeches by the honorable minister, who outlined Bangladesh’s views on cyber matters. Keynote Talks then highlighted various national perspectives on cybersecurity before the participants attended their chosen sessions.
In the first Opening Speech, Mr. Zunaed Ahmed Palak, MP stressed the importance of securing the availability, openness, and integrity of the internet through international cooperation at the level of the state, the private sector, and civil society. The Minister noted that the internet and IT infrastructures have brought a wealth of opportunities to the global community by facilitating trade and communication. He emphasized that, from the start, cyberspace has been a global, open network that has reinforced education, technological innovation, and the exchange of knowledge and ideas. Moreover, he argued that this space of freedom, personal development, and economic progress warrants protection. According to Mr. Palak, security and freedom are complementary – without freedom, security could become repressive, and without security, freedom would cease to thrive. Cooperation between international stakeholders is required to manage and preserve a secure and free cyberspace. Consequently, “cyber-diplomacy” discussing and negotiating internationally accepted rules of behavior – is taking place in various international forums and regional organizations which accords with the complexity of the subject.
Honorable secretary of ICT Ministry stated that Cyber security is of paramount importance. Recent cyber attacks in Bangladesh and in the neighboring countries have proven the importance of cyber security. Computer incidence response team was set up last year and he expects that CIRT will continue its good work in handling and security. He hopes the team will keep its focus on its security. Lastly, he thanked the organizers of the conference and wished its success.
Mr Rimanta Žylius, previous Minster of Economy, Lithuania was the first key note speaker. He was responsible for setting up the NRD in Lithuania. He mentioned that the ICT minister is not responsible for security of all institutions. All institutions must protect themselves. He stated that we need to understand where we are going. We need to understand whether our organization’s management is operating it in a secured manner. He asked an important question of “What happens if some rooms go down, it our organization still usable? Have we tested it?” Another important question he asked was that “Does employees who left organization still has access control?” Mr. Zylus also stated the fact that technology alone will never succeed, it needs efforts from the management. Clear mandate and transparent reporting will be essential for its success.
Next, Certificates of Ethical hacking was handed over by Hon. Minister, to the certified ethical hackers of the country. The certified hackers came up to the stage and received their certificates. Afterwards, CID personnel who participated in Oxygen Forensic were handed over the valuable certificates.
BGD e-GOV CIRT team member Mr. Debashis Pal & Mr. Mohammad Ariful Islam presented the second key note speech on Cyber Security trends within the Government of Bangladesh: Case study from BGD e-GOV CIRT. Beginning of the presentation, they had shown BGD e-GOV CIRT activity, registered incident amount & sample case studies from their experience. Two real life cyber-attack demonstration was shown by them. During their presentation, they informed audience if the top management follows international process standards (e.g. ISO 27001, ISO 17799 standards), then if the System architect/system manager follows Critical Security Controls (CSC), if the web application developer follows Open Web Application Security Project (OWASP) developer guide & execution engineer to follow Center for Information Security (CIS) benchmarks, then a good cyber defense strategy will be developed.
One World USA then gave presentation on Cyber Security Imperative.The motto of this keynote speech was “Sooner the threat to the critical infrastructure is detected the sooner we need to take some precautions.” Some of the focus areas of this presentation were Effective vulnerability management, Penetration testing, Privileged account safety and Detection and Rapid response of cyber incidents.
Moritz Raabe, analyst of malicious software and programs of FireEYE presented the malwares in Point of Sales (PoS) machines. He showed how to dissect malicious software by taking malware traffic and analyze to identify set of commands executed by the attacker. He mentioned that malware analytic is different from forensic investigation. Through basic analysis and advanced techniques they have developed the IDA Pro tool for malware detection via signatures.
Cisco made presentation on Security Challenges and Minimizing risks: Best practices highlighting the fact that PoS machines and ATM machines are running in Windows XP which has a lot of vulnerabilities. They also suggested to look into Cisco’s annual security report. The experts highlighted that Cloud will bring forward a lot of challenges. Both from public sector and private sector perspective. Lot of SaaS based services. He stated that Adware was initially designed to earn money. According to Cisco, Budget, compatibility issue, lack of professionals, lack of certification requirements are the main barriers to security.
Reve Systems presented their Alapon software for communication between government officials and sharing of important government files and information. They informed that Alapon’s storage is at BCC data center and it is LI compliant. Directory service for finding government workers is also provided in Alapon. The features of Alapon include Audio and Video Calling, sharing of files, location tracking facility (controlled by the user, optional). The system is secured with RSA, 128-bit key. In the future, 2FA SSH and Black Box for the server will be introduced.
Declaration 2017 on Strengthening Cyber Security
Mr. Tarek Mosaddek Barkatullah, director of Bangladesh Data Center, presented the declaration. Declaration was read and agreed by the participants of the conference. Afterwards incorporating their comments on it and also suggestion, Minister signed the declaration. The signed copy of the cyber security declaration adopted by Bangladesh government can be found here.
Mr. Tarek Mosaddek Barkatullah, director of Bangladesh Data Center then delivered gift to the Honorable Minister of Economy, Lithuania for his contribution to CIRT in Bangladesh. Goal is to develop more secure Digital Bangladesh.
Conference outcome: Food for Thought
From the point of view of the CIRT and BCC, which organized the conference, intense presentations, discussions, and Closing Panels led to the following observations, which should guide the development of further research questions and policy responses:
- The cyberspace is part of the daily life of many citizens, companies, and governments. Cyberspace entails not only ground-based assets and critical infrastructures, but also wireless communication and space-based platforms. Cyberspace is fast-growing and its technological, legal, industrial, political, and military implications have not been fully explored.
- A larger framework, including international cooperation, is needed for the establishment of norms and rules for adequate, responsible state behavior to ensure and guarantee the peaceful use of the cybersphere.
- Passwords should not be simple and needs to be as complicated as possible to make it difficult for the malicious activists to break them.
- There is a wide range of possible measures to prevent the large-scale build-up of offensive cyber attack capabilities and their use, starting with confidence and security building measures in cyberspace and the development of a national code of conduct. However, definitions will need to be agreed in advance. One option for kick-starting this process would be for the country to make unilateral declarations aimed at preventing large-scale harm to the 22 critical infrastructures.
- The attribution of large-scale cyber attacks is not easy, but may be possible under some circumstances. Threat detection and diagnostic forensics therefore can and must be improved. Also there is an increasing need for training on cyber security.
- More and more countries are establishing national security cyber commands. These states should make their cyber doctrines public – explaining their offensive and defensive motives, measures, and resources. Organizations such as the CIRT should continue to organize annual seminars to discuss capabilities and perceptions of national cyber strategies as a further trust-building exercise.
- Individual government organizations should be responsible for protecting cyberspace assets located on their territory. This requires them to cooperate to exchange technical and procedural information about the protection of ICT vulnerabilities, especially in times of crisis. Early warning, quick responses, and adequate stabilization measures are vital; less-developed countries should receive support from technologically advanced nations.
- Despite political and ideological differences, more multi-stakeholder conferences (such as the follow-up events to the Cyber Security Conference 2017) complemented by bilateral and multilateral consultations between governments and, most importantly, regional and international organizations are necessary in the years to come.
Recommended Posts
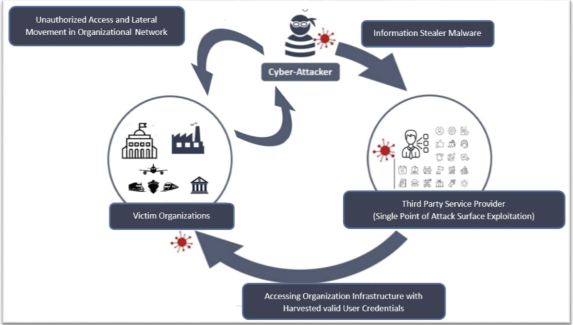
Cyber Threat Alert: Surge in Attacks via Compromised Third-Party Service Providers
08 Feb 2024 - Articles, English articles, Security Advisories & Alerts